Maximizing Business Security with MDM Solution
Q: What is Mobile Device Management (MDM)?
- MDM is a software solution used to manage a fleet of mobile devices like smartphones, tablets, and laptops. Enterprises of different sizes primarily use MDM solutions to manage and control company-owned devices.
Almost every industry, including transportation, healthcare, IT, retailers, and hospitality, uses MDM solutions to get device visibility and manage device access.
Data on devices is highly confidential, and its breach can damage the reputation of companies. Businesses prefer MDM solutions to safeguard the company’s data and remotely troubleshoot issues. It also helps businesses to schedule updates for regular device maintenance. MDM security policies allow businesses to remotely control the apps, content, and security of devices so the employees can work effectively without worries.
Part 1. How MDM Enhances Enterprise Security?
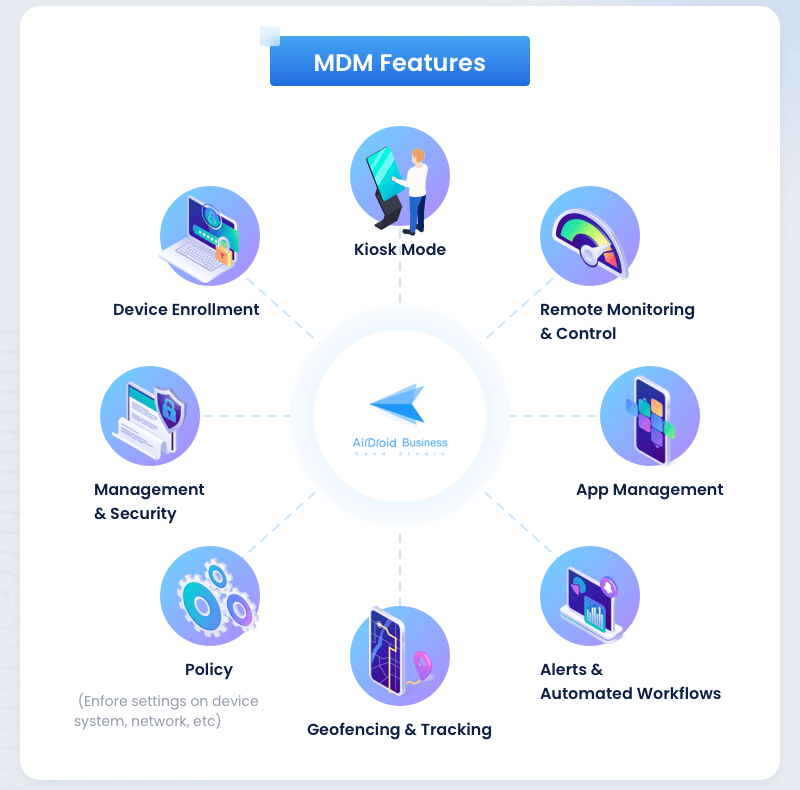
MDM provides kiosk mode, app management, and location tracking features to enterprises so they can better manage the security of devices.
- Kiosk mode enables admins to implement single-app or multi-app kiosk mode to allow specific apps to run on devices. Admins can also lock down the devices with specific websites. It helps to prevent unauthorized access to system settings and sensitive data.
- MDM also helps businesses to track real-time locations of devices to ensure their security, and admins can remotely lock down the devices if found unsafe. Companies can improve productivity by watching location history and the stay time of devices at a specific position.
- Admins can remotely manage the application access on devices to enable employees to focus on assigned tasks. Admins can apply test releases on a few devices to identify app bugs before configuring them on all devices. It helps to ensure continuity of work with reduced risk of downtime.
Part 2. Maximizing Business Security with MDM Solution
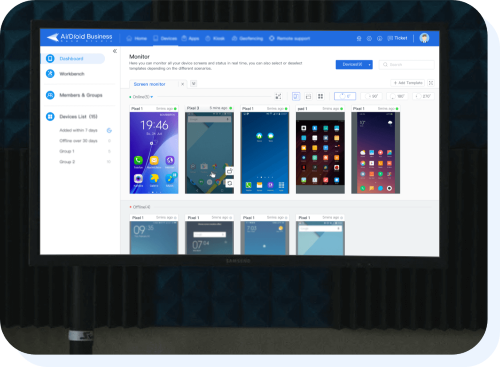
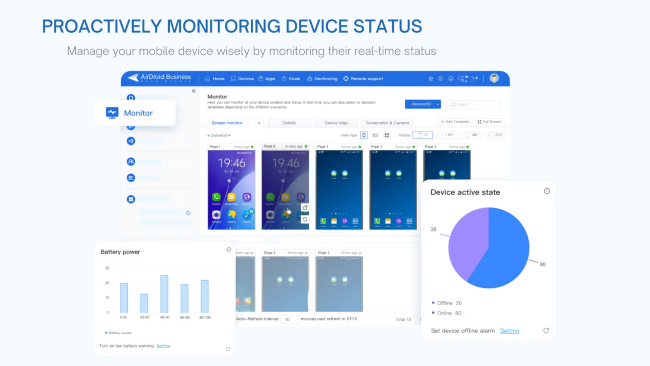
Monitor company devices in one dashboard
MDM solution provides a single and user-friendly interface to monitor and access a large number of devices. Admins are given complete access to check insights of each device. They can also remotely diagnose and troubleshoot issues on devices to reduce downtime.
MDM security policy
The policy offers a wide range of settings including password management, device limitations, and general settings.
- Admins can set strong password inputs and multi-factor authentications to restrict device usage for unauthorized users.
- Device limitations include functionality limitations like sound or volume recording, compliance management, and safety modes like developer mode, safe mode, and factory reset.
- General settings include managing VPN, APN, device language, and time zone.
Real-time location tracking
MDM allows businesses to track the real-time location of managed devices when required. Admins can view the device history route and stay time, to consider each factor while analyzing the performance of employees.
In the transportation and logistics industry, it helps to track the location of heavy vehicles and provide instant support if any issue arises.
![]()
Prevent devices from being stolen and lost
Businesses use MDM to track the real-time location of devices and find lost devices easily without trouble. MDM helps them to lock down the devices remotely if remain unlocked. Businesses can also remotely wipe, or factory reset the devices if they are unable to recover the device so no one can breach their privacy.
Create alerts for irregular behaviors
MDM allows businesses to set alerts for various uncertain conditions that can interrupt device usage and create other issues. For example:
- Admins are timely notified when the battery or storage of devices is about to end.
- Geofencing helps to alert admins when devices reach a restricted area so they can take quick actions accordingly.
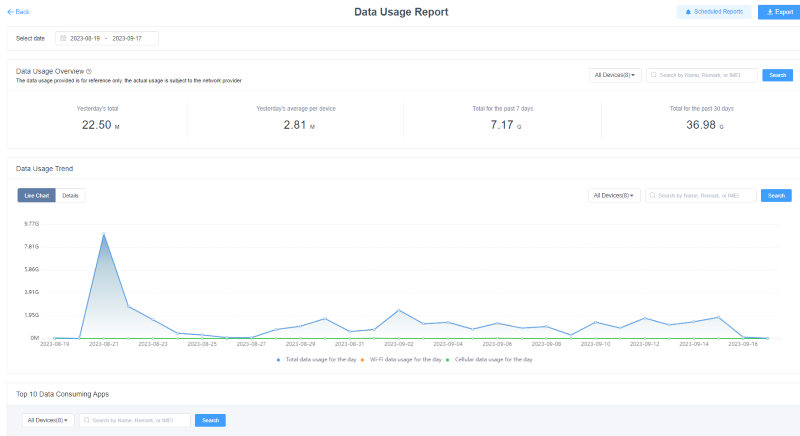
View analysis of device data usage
MDM provides a comprehensive report on data usage, displaying data usage on each app. It also gives information about frequently used apps. Admins use this information to analyze the performance of employees and optimize their device usage during working hours.
App management
Admins can use test releases before deploying apps on all devices. It helps them to test and release the app on a few devices to check the app for bugs. It ensures the continuity of the devices without issues. MDM also enables the forced installation of apps on devices when they are unattended.
Kiosk mode
The kiosk mode of MDM allows businesses to lock devices to specific apps and websites. Businesses provide self-service devices with kiosk mode to automate their tasks. You can use single or multi-app kiosk mode to limit the application usage on devices.
We recommend AirDroid Business MDM here for Android devices because it offers various features like policy, app restrictions, and remote monitoring to manage the security of devices. It offers a 14-day free trial and flexible pricing for different business sizes.
Part 3. How Secure is MDM?
Some businesses may worry that they can't judge which MDM solution meets the security standards that their company demands. Here are some security points that we have listed for your reference.
Data Encryption
When choosing an MDM, businesses must consider data encryption. It is a fundamental aspect of cybersecurity that keeps the data secure while sharing. You need to consider various encryptions like TLS, which keeps your data safe when transferring.
Compliance and Security Policies
Companies need to know what security features are required to secure their devices. Every industry has specific regulations that companies have to comply with. MDM provides manageable security measures for businesses to meet standards of security.
Remote wipe or Factory Reset
There are various situations in which businesses need to secure devices from unauthorized access. MDM's remote wipe or factory reset feature allows enterprises to wipe data from devices when found in unsafe hands remotely.
Reporting and Monitoring
Businesses need to analyze employee device usage to improve productivity and security by optimizing device usage. MDM provides precise data for each device usage to ensure devices are using safe and necessary apps.
Part 4. How to Start MDM for Security Management?
Most MDM solutions offer web-based consoles for better management. The following is an example of using AirDroid Business for security management:
- Step 1.Create Account
- Click the free trial button and register an AirDroid account for device management.
- Step 2.Open Admin Console
- Use credentials to log in to the admin console.
- Step 3.Enroll Devices to AirDroid Business Admin Console
- Enroll enterprise-owned devices with the admin console using any methods it supports. You can enroll devices using a deployment code, an auto-enroll package, zero-touch enrollment, or a USB connection.
- Step 4.Create Config File
- After successfully enrolling the devices, customize the settings using the admin dashboard to start management of the devices as per your requirements.
Part 5. What OS Devices Can be Managed with MDM?
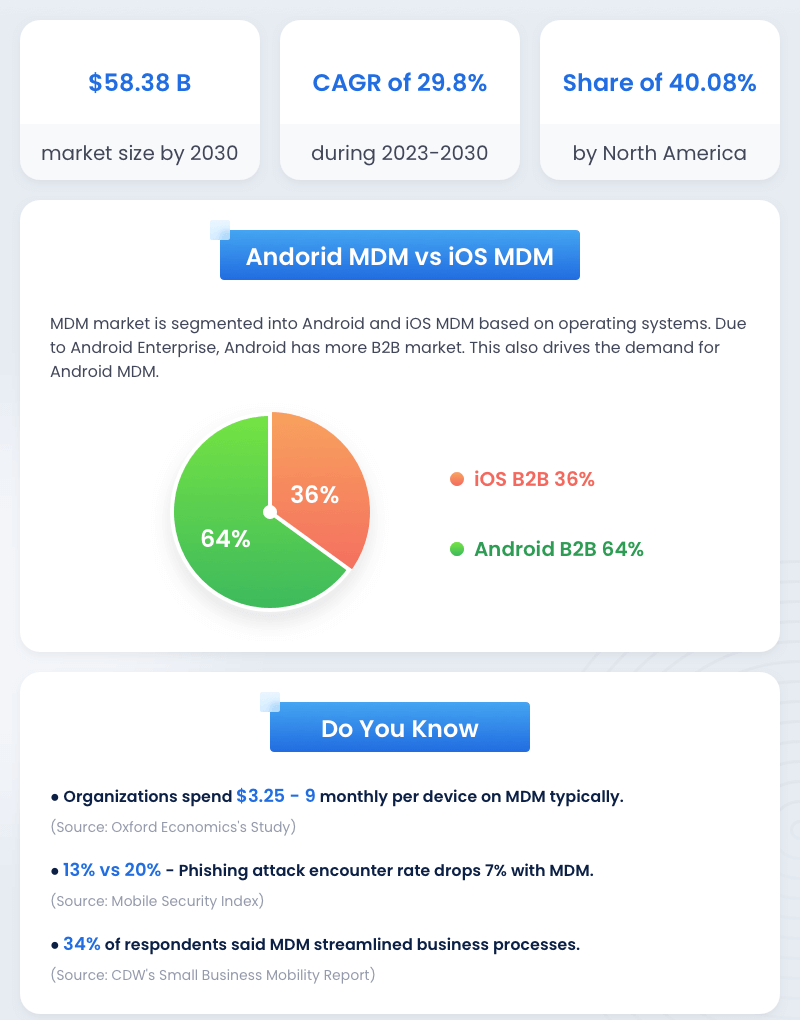
Depending on their capabilities, MDM solutions can manage Android, iOS, Windows, and Linux because most are made for specific operating systems. Management of iOS devices using MDM is comparatively challenging because of Apple’s high-security measures. Apple also offers limited customization to provide a consistent interface. Moreover, MDM may have limited access to device information due to the high privacy restrictions of the Apple OS. Alternatively, Android devices are highly customizable and easily integrated with MDM solutions. It is one of the primary reasons most businesses prefer Android OS to get better device visibility.
Part 6. The MDM Terms You Should Know
BYOD
BYOD stands for Bring Your Own Device. It is a business model that allows employees to bring their own devices for official purposes. Security risks for such businesses are very high as employees are free to use them. So, enterprises need to efficiently manage their security on such devices using MDM solutions. MDM will create a balance between personal and professional usage.
OTA
The abbreviation for OTA is ''Over-the-air.'' It is a term used in the IT industry to explain the concept of wireless support and connection. Data sharing and control over devices from a single device is managed using OTA. Various businesses utilize OTA to remotely update apps, streamline the device installation process, automate security patches, and troubleshoot errors remotely.
Device Enrollment
It is a process of adding and configuring devices into a system or network. Businesses use various methods to enroll devices into management systems to manage and control business-owned devices remotely. Zero-touch enrollment is the most convenient and fastest method to deploy a fleet of devices simultaneously.
Containerization
Business models like BYOD need containerization to save corporate data separately on employees' devices and ensure high-security features. They are highly scalable, and companies can save and manage corporate data in containers easily.
Compliance and security policy
Compliance is the regulation set by various industries that every organization has to follow to ensure smooth and uninterrupted working.
Security policies are the measures that enterprises can utilize to comply with regulations.
Part 7. Tips: How to Successfully Implement MDM for BYOD?
Implementing MDM on BYOD is a complex process as it involves balancing user privacy with official policies so that user privacy is not affected by security policies. MDM remote monitoring and controlling in BYOD should only be applicable during working hours with no access to the employee's data.
Define clear BYOD policies that fulfill business security requirements and also respect employees' privacy. Choose an MDM solution that can comply with your company's BYOD policies. Use containerization to keep personal and corporate data separate. You can also add strong password and authentication policies and an easy deployment process with automation.
Conclusion
MDM security helps businesses to enhance security measures and safeguard the data by providing customizable security policies. It also helps them to comply with various industry standards. MDM is the most secure software solution for different businesses. Different MDM software has compatibility with different operating systems like Android, Windows, and iOS. You must choose a solution that is compatible with your business-owned devices and provides all the features to comply with regulations.
FAQs
When using Remote Control, the controller can enable Black Screen Mode to avoid interference from the remote device. You can enable Black Screen Mode on Windows, Mac OS and Android as a controller.
In Black Screen Mode, the remote device will be screened and shown as it is under maintenance. It prevents the end-users or passersby from seeing what is happening on the device. With this feature, businesses can protect their corporate privacy at all times.
Please note that this feature is only available for Standard and Enterprise users.





Leave a Reply.