Protecting Your Clients: A Guide to Preventing MSP Hackings
While Managed Service Providers (MSPs) have indeed become indispensable for modern businesses to hand off their IT infrastructure, network security, and software management, however, this hasn't come without risk.
MSPs are now a prime target for cybercriminals due to the nature of their central role in managing, in many cases, more than one organization's IT environments, with the potential of a breach impacting multiple organizations in a single strike.
The MSPs industry is more susceptible to cyber attacks than other industries. The screenshot below shows the most common security incidents in the cloud for MSPs compared to other industries:
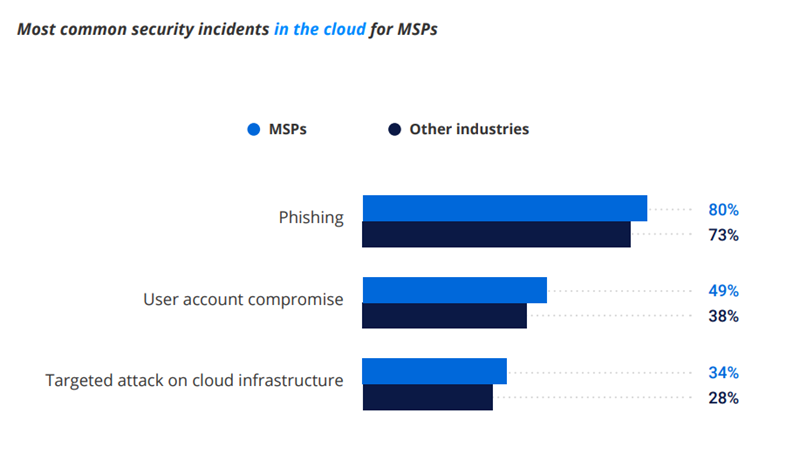
Netwrix Hybrid Security Trends Report 2024
The data indicates that MSPs experience a higher percentage of these security incidents compared to other industries, especially in phishing.
Part 1: Why Hackers Target MSPs
Here are some reasons why MSPs have become such a valuable target for hackers and malicious actors:
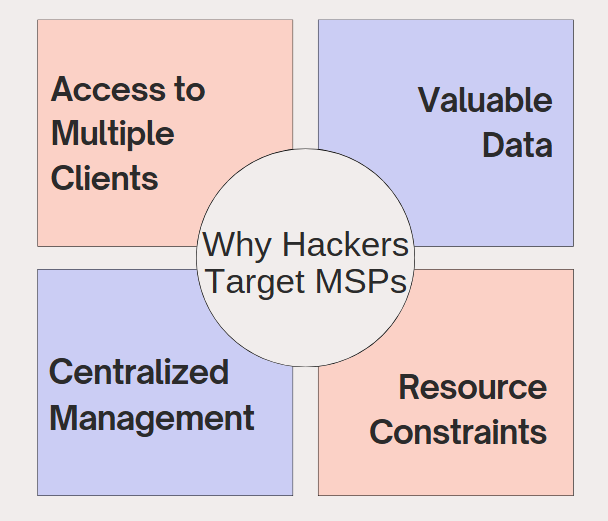
Access to Multiple Clients
One of the biggest contributing factors to MSPs now becoming a target for hackers is that it serves as a 'hub' that connects multiple client systems. In most cases, MSPs have direct administrative control of their client's IT infrastructure, which makes them a one-stop shop to infiltrate and attack dozens, if not hundreds of networks.
90% of MSPs Suffer Successful Cyberattacks in 2021 and 2022, and most MSP companies say they are always under the cyber security threats.
MSPs essentially serve as a single point of entry to amplify their attack. If they find a vulnerability to get access into the system, that may compromise the data and IT environments of their entire client list.
For example, in 2021, Kaseya experienced a ransomware attack via a vulnerability in their software, and hackers were able to deploy malware across numerous customer systems simultaneously.
Valuable Data
MSPs manage incredibly sensitive & confidential data for their clients which can include personal information, intellectual property, financial records, and system credentials.
With this information in hand, cybercriminals can exploit this data in multiple ways; selling it to the highest bidder on the dark web, identity theft, or ransoming and extorting businesses.
According to the PR Newswire report, each second security incident in the cloud (49%) was associated with user account compromise, and some are other important user data.
The intrinsic value of this data and its potential accessibility via MSP platforms make it a lucrative target. For instance, healthcare clients that rely on MSPs are completely vulnerable since patient records are highly sought after and fetch high prices on black markets.
Centralized Management
Centralized management tools like Remote Monitoring and Management (RMM) software while invaluable for MSPs, also have the potential to be double-edged swords when the system is compromised.
With these tools, attacks can leverage RMMs to bypass client defenses such as accessing any system on the IT infrastructure to disable antivirus systems and execute malware through 'fake' updates using administrative privileges.
Resource Constraints
Some small-to-medium sized MSPs are often limited in resources which limits their ability to invest and focus on implementing robust cybersecurity measures.
These constraints leave them vulnerable even to less sophisticated attacks depending on their existing cybersecurity teams and systems, and if they've implemented proactive monitoring properly.
Part 2: Common Cybersecurity Risks Faced by MSPs
This part introduces the common cybersecurity risks faced by MSPs:
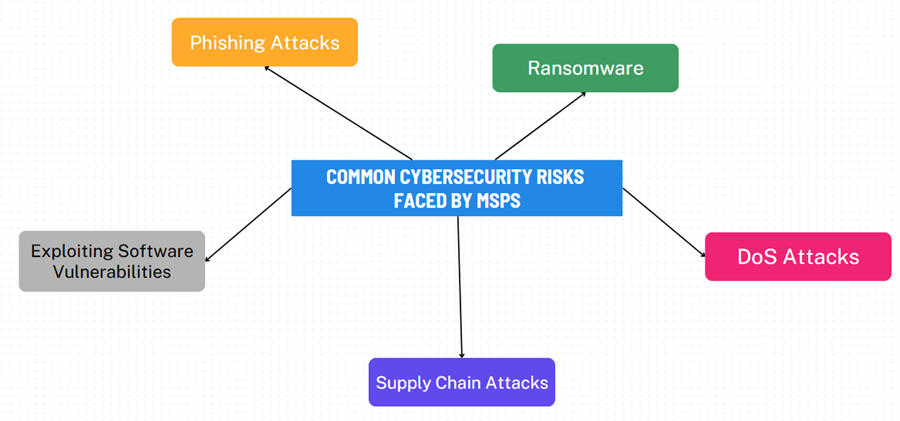
Phishing Attacks
While many regard phishing attacks and attempts to be a mostly inconsequential form of cyberattack they couldn't possibly fall for, in the modern era, cybercriminals have the ability to craft highly convincing emails and messages that almost perfectly impersonate trusted entities down to the format of the message and the sender details.
This can still trick employees at an MSP into revealing login credentials or downloading malware.
When a phishing attack is done at scale (to hundreds of employees), it only takes one breach of a user with administrative privileges to access client data and attack systems from within.
Ransomware
Ransomware has evolved into sophisticated operations to maximize disruption, and for targetted MSPs, this can be doubly as devastating.
Since cybercriminals can gain access via unpatched vulnerabilities or phishing attacks, they can deploy 'ransomware' which is a type of malware specifically asking to be paid a certain amount before the end user can access their systems/files.
This is done once they have access to an MSP's centralized tools like RMM software, which deploys the ransomware across client systems. This has the potential to be catastrophic if the hackers can access multiple client's IT infrastructures by attacking just one MSP.
Exploiting Software Vulnerabilities
MSPs are already a 'third-party' used to manage a business's IT environments, but MSPs themselves typically rely on third-party software to help manage client operations. However, this provides hackers with another route to exploit if there are any unpatched software vulnerabilities with these third-party tools.
Supply Chain Attacks
Alternatively, instead of attacking the MSP's third-party software, hackers could instead launch a supply chain attack, directly compromising a trusted vendor/software to infiltrate MSP systems.
Since these attacks bypass the traditional security measures in place because they're exploiting the inherent trust in vendor relationships, supply chain attacks can be more intrusive and 'undetected' than other cyberattacks.
Denial of Service (DoS) Attacks
A DoS attack is a type of cyberattack where malicious actors deliberately overwhelm an MSP's infrastructure with excessive traffic or requests, resulting in a disruption to operations and preventing users from accessing critical systems.
For example, hackers could launch a DoS attack on an MSP's web portal which is used by clients to send support tickets or for system management. Clients/users would then not be able to access the system, leading to crashes or becoming unresponsive.
DoS attacks are also used as a diversionary tactic for more targeted intrusions. These types of intrusions/disruptions can be detrimental to an MSP's reputation, undermining client confidence in their services.
Part 3: How to Prevent MSP Hacking: Tips & Factors to Consider
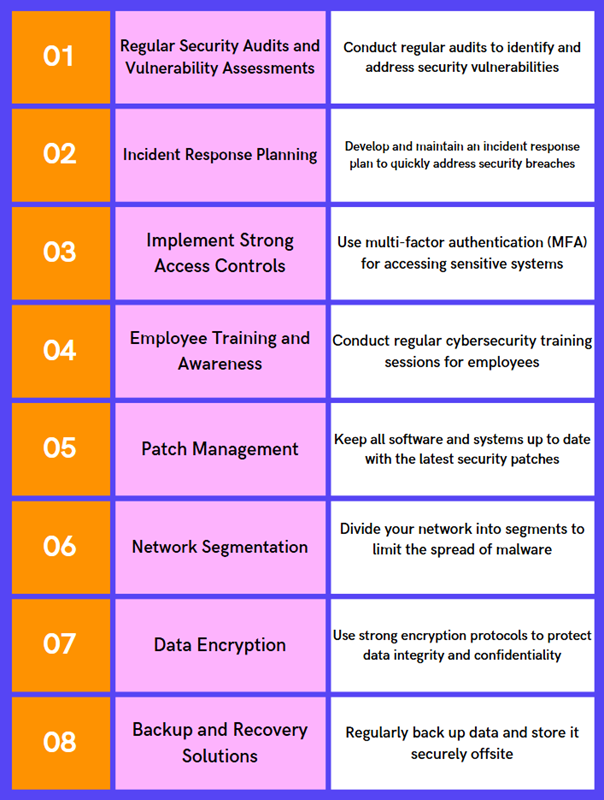
Regular Security Audits and Vulnerability Assessments
Routine audits are crucial for identifying vulnerabilities before attackers can exploit them. This includes reviewing and assessing an MSP's infrastructure, policies, and procedures to identify weaknesses.
This can include multiple tests such as penetration testing to simulate attacks on your network to find exploitable vulnerabilities, configuration reviews to ensure firewalls and other security measures and configured correctly, and compliance checks.
As an example, if an MSP conducts penetration testing and finds that some employees have weak or easily cracked passwords. Once identified, the MSP can strengthen and review password policies or implement multi-factor authentication to mitigate the risk.
Incident Response Planning
In the unfortunate circumstance there is an intrusion, a robust incident response plan ensures an MSP can react swiftly and effectively during a breach.
This includes clearly defining roles and responsibilities to IT staff, a playbook to respond to specific scenarios and attacks with detailed response steps, and conducting regular drills to test readiness.
It might also be useful to deploy an incident response platform to help automate and streamline workflows in the event of a breach. With a well-executed plan, MSPs can significantly reduce downtime and limit the potential fallout and impact of a breach.
Implement Strong Access Controls
Access management is a cornerstone of cybersecurity and can include multiple aspects for stricter control. This can include measures such as Role-based access control to restrict access to specific systems and data based on job roles and multi-factor authentication to verify and strengthen login processes into sensitive systems.
Additionally, MSPs can also utilize privileged access management tools to help manage and monitor 'privileged' accounts with overarching control and access that other accounts do not have.
This way, MSPs can directly monitor who, when, and where admin credentials are used and can detect unusual activity to take the appropriate response.
Employee Training and Awareness
As much as you can safeguard and improve security measures technology, the true 'weakest' link of the IT infrastructure is often humans. That said, it's important to hold regular employee training to ensure they're aware of potential dangers to look out for.
This could include updated phishing awareness campaigns to teach employees how to identify fraudulent emails and training them to properly report incidents for any irregular activity even if it turns out to be a false alarm.
Another important 'training' employees should go through is password hygiene. Ensure they're creating and using strong, unique passwords with special and alphanumeric characters.
Including a regular password update schedule (every 6 months, after a year) could also be beneficial.
Patch Management
One of the most exploited vulnerabilities for many MSPs is unpatched systems and software. Software and tools that are not up to date do not have the required protections it should have, making it vulnerable to misuse and acting as an unauthorized access point.
To counteract this, MSPs should look into using tools that automate the deployment of patches such as Windows Server Update Services. These systems can track, test, and apply patches across the MSP's infrastructure.
Regularly updating firmware, operating systems, and applications minimize exposure to known exploits.
Network Segmentation
Segmenting networks help to limit the movement of attackers in an environment. By isolating client environments from internal MSP systems, breaches are contained more effectively to specific networks instead of the entire IT environment.
This includes separating client networks so that each client's infrastructure is isolated from others in the event of a breach or using micro-segmentation tools to divide internal systems into smaller, isolated segments.
Data Encryption
Assuming that attackers do gain access to critical data, properly encrypted data in both transit and rest ensures that even if malicious actors can access this information, it is unreadable and unusable without the appropriate decryption keys.
Using advanced protocols like AES-256 for stored data and TLS for transmitted data helps to add an additional layer of security for the MSP's clients' sensitive data even if breached.
Backup and Recovery Solutions
Lastly, MSPs should create and manage multiple reliable backups to minimize the impact of disruptive and destructive attacks. For example, MSPs should consider adopting a '3-2-1' rule for their backups.
This means MSPs should hold and maintain three copies of client data, stored on two separate and different mediums, with one of these backups stored offsite and separated from the rest of the MSP's IT environment.
Additionally, regularly testing the backup restoration process to ensure data can be recovered quickly in an emergency is a good routine practice to follow.
Part 4: How MSP Hacks Affect Clients
Client Trust Issues
For MSPs, how much your clients trust you directly impacts your real-world performance.
If clients' trust is in any way diminished, MSPs could lose out on contracts since clients are afraid of further attacks and the inability of the MSP to safeguard their IT infrastructure and sensitive company data.
This would have a domino effect, eventually leading to a long-term, tarnished reputation the MSP may not be able to recover from.
Data Loss and Exposure
A successful attack opens up a client's sensitive data, customer information, and trade secrets to exposure. This could lead to both data loss as well as compliance violations which could impose financial penalties under regulations like GDPR and CCPA.
Operational Downtime
Another key factor of how a hack can affect an MSP's clients is in their daily and regular IT operations. Cyberattacks can disrupt these services and cause delays or lost productivity, but they can also cause significant financial losses if the MSP is unable to maintain seamless IT operations.
Financial Consequences
Besides potential ransomware demanding money, cyberattacks also have other aspects that can cause a financial burden on MSPs and their clients.
51% of MSPs have to deal with unplanned expenses to fix the security gaps. Moreover, 31% experienced a loss of competitive edge.
This can include forensic investigation and legal fees for the breach, regulatory fines for clients, lost businesses, and other additional expenditures to enhance security measures.
Part 5: Real-World Examples of MSP Hacks
Case 1. SolarWinds Hack
Disclosed in December 2020, the SolarWinds hack is one of the most significant supply chain attacks in recent history, compromising numerous global organizations. Attackers injected malicious code into SolarWinds' Orion software updates, and are estimated to have been distributed to over 18,000 customers.
The backdoor, known as 'Sunburst' provided attackers access to several entities' networks, including U.S. government agencies and private companies.
For now, the breach is still under investigation but needless to say, the damage was significant even to tech giants such as Microsoft, Intel, and Cisco.
Case 2. Travelex Ransomware Attack via MSP
Travelex, a major foreign exchange company suffered a massive ransomware attack in December 2019. The hackers exploited unpatched vulnerabilities in the company's systems, resulting in widespread operation disruptions.
This caused Travelex's online services to go offline and even affected in-store operations.
The hackers demanded a $6 million ransom and paired with the Covid-19 pandemic at the time, Travelex eventually went up for sale due to financial instability & potential bankruptcy of the parent company, Finablr.
Part 6: Final Words
That said, MSP hacking can have a devastating impact so it's a good idea to be extra cautious in all aspects.
The key, however, seems to be in the prevention and proactive measures in place against cyberattacks rather than reactive measures once the breach has already taken place.
Your first line of defense should be strong enough to not have to rely on reactive measures like encryption and backups in the first place, but it's also crucial to ensure both aspects are thoroughly covered to ensure your client's IT infrastructure and sensitive data are protected.











Leave a Reply.