Samsung Knox Service Plugin (KSP) Deployment Guide
Samsung devices have become a core part of business operations thanks to their flexibility, but that same flexibility can lead to security risks and management complexity.
That’s where Samsung’s Knox Service Plugin (KSP) comes in, helping IT teams enforce advanced policies and streamline control across large device fleets.
Still, many admins struggle to integrate KSP with existing MDM solutions. This guide explains how to deploy KSP effectively and fully activate features often left unused on corporate Samsung devices.
1What Is Knox Service Plugin (KSP)?
KSP is an app designed specifically for enhanced management and policy configuration on enterprise devices supporting the Knox platform. It’s Samsung's solution based on OEMConfig. Think of it as a specialized toolkit that unlocks Samsung-specific features that generic MDM solutions can't access on their own.
With Knox Service Plugin App integration, you can configure an impressive array of policies, including:
- VPN settings and secure connections
- DeX functionality for desktop-like experiences
- Granular device restrictions (Wi-Fi, Bluetooth, microphone)
- Robust password policies
- Certificate management for secure authentication
- Firewall and proxy configurations
- DualDAR encryption for sensitive data
...
The plugin essentially serves as a translator between your MDM platform and Samsung's proprietary hardware features, giving you access to Knox capabilities without requiring custom development or API integration.
Implementation Requirements
- To access the full capabilities of the Knox Service Plugin App, you’ll need devices running Android 9.0 or higher with Samsung Knox 3.2.1 or later. While limited functionality may be available on Android 8.0 with older Knox versions, many advanced policies, including DualDAR encryption and certain certificate features, require the newer platform versions.
- You'll need an existing MDM/UEM/EMM platform. KSP isn't a standalone solution. It's distributed through Managed Google Play Store and works alongside platforms like AirDroid Business, MobileIron, VMware Workspace ONE, and others to push configurations to your devices.
These requirements represent the foundation needed to create a robust management environment where KSP can perform at its best.
2KSP Deployment Processes
If you're already using an MDM solution, deploying KSP will follow a similar workflow to what we'll describe in this admin guide.
You'll simply need to locate the corresponding options in your MDM's admin console and upload the Knox Service Plugin App as needed.
However, if you're looking for a deployment solution that satisfies Samsung's security requirements without incurring high maintenance costs, AirDroid Business offers an excellent balance of functionality and affordability.
Let's explore the process of deploying KSP using AirDroid Business as our example:
OEM Configuration
Start by accessing the AirDroid Business admin console and opening the policy configuration section. From there, select the Samsung OEMConfig profile, which supports configurations for managed devices.
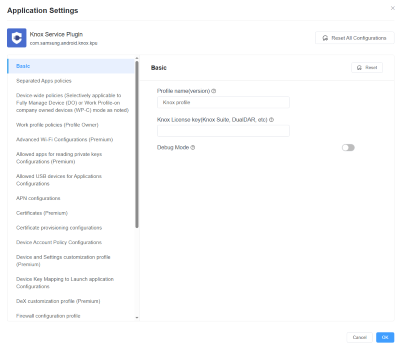
This profile exposes Knox-specific settings, such as security policies (password rules, DualDAR), network rules (VPN, Wi-Fi control), and device restrictions (camera, Bluetooth, microphone).
Admins can configure work profiles by department or use case. For instance, apply stricter policies for finance teams while allowing sales teams to control access to hardware features. Use role-based groups to simplify policy assignment and future updates. Keep in mind that some advanced settings may require a premium license.
Once configured, save the policy and assign it to your designated device group within the console.
Automated Distribution
Once your policies are configured, it's time to push them to your target devices. Here, KSP offers seamless deployment across your entire Samsung fleet.
With AirDroid Business, this process is straightforward:
- Select your target devices or groups
- Assign your configured KSP policies
- Initiate the policy push
The system will automatically distribute the KSP app and your defined configurations to all selected devices. Most policies take effect immediately upon installation, though some may require a device reboot.
One of the best features of KSP distribution is its intelligent handling of device compatibility. If you've included devices in your deployment that don't meet the minimum requirements for certain policies, KSP will apply only the compatible settings rather than failing entirely.
During this phase, it's wise to start with a small pilot group before rolling out to your entire fleet. This allows you to identify and resolve any issues in a controlled environment before affecting your broader organization.
KSP Updates
Mobile security is a moving target. Samsung regularly updates KSP to address new security challenges and add functionality. Its updates are managed via Google Play. AirDroid Business supports custom app update configurations through managed app settings. While there's no built-in toggle for automatic KSP updates, admins can define update behavior by setting app update policies for managed apps.
Schedule updates during low-usage periods and test them with a control group to avoid disruptions. KSP updates are usually backward-compatible, but new policies might require review before broad rollout.
3KSP Configuration Issues and Solutions
Even the most carefully planned KSP deployment can encounter challenges. Understanding common issues and their solutions will help you troubleshoot effectively and minimize downtime.
1Issue 1: Policy Conflicts and Deployment Failures in KSP
One of the most frustrating experiences in KSP management is configuring policies that either conflict with each other or fail to deploy successfully. For example, you might configure a screen timeout setting that never actually takes effect on your devices.
These issues typically stem from one of three root causes:
- Policy conflicts between KSP and existing MDM settings
- Compatibility issues with specific device models or Android versions
- Network connectivity problems during policy deployment
The solution lies in systematic troubleshooting. Start by examining the logs from both KSP and your MDM platform. These logs often contain valuable clues about what went wrong during deployment.
While KSP updates are distributed through Google Play, automatic or manual update control for managed apps (including KSP) depends on how app update policies are configured within your MDM.
In AirDroid Business, update behavior for managed applications may require manual handling or scheduled deployments depending on the admin's app management settings.
Check your admin console for available controls related to Play Store app update policies. Look for error codes or failure messages that might indicate the source of the problem. If you see conflict warnings, review your policies for contradictory settings.
For example, KSP might try to enforce a one-minute screen timeout while your base MDM policy specifies five minutes.
For persistent issues, try deploying policies individually rather than in batches. This helps isolate problematic settings and narrows down where the conflict is occurring.
2Issue 2: Balancing Security and Flexibility in KSP Configuration
Finding the right balance between stringent security controls (like DualDAR encryption and VPN requirements) and user flexibility (DeX mode configurations and personalization) is a perennial challenge in enterprise device management.
Too much security can hamper productivity and frustrate users, while too much flexibility can create security vulnerabilities. This balancing act is particularly challenging with KSP because it offers such fine-grained control.
The most effective solution is to implement role-based policies that align with job functions and security requirements. For example:
- Executives handling sensitive data might receive maximum security configurations
- Field technicians might need more hardware flexibility, but strict VPN requirements
- Office staff might have moderate restrictions balanced with productivity enablement
By grouping your devices according to use cases rather than applying blanket policies, you can craft configurations that make sense for each role in your organization. Start by identifying your security non-negotiables (the policies that must be applied universally) and then build role-specific configurations around those core requirements using role-based access control. This approach satisfies both security mandates and operational needs.
4Final Word
Deploying the Samsung Knox Service Plugin effectively can transform how you manage your enterprise's Samsung device settings. By unlocking the full potential of the Knox platform, you'll gain access to advanced policies and security features that help protect your organization's data while streamlining management processes.
The right KSP implementation allows you to define policies that align with enterprise regulations, significantly reduce the risk of human operational errors, and elevate your overall device management and compliance posture. While the initial setup requires careful planning, the long-term benefits in security, efficiency, and control make it well worth the investment.
Remember that mobile security requires ongoing attention and adaptation. Make KSP a cornerstone of your mobile security strategy, but be prepared to evolve your approach as both threats and business needs change over time.
The principles outlined in this guide will help you create a more secure, manageable, and productive mobile environment for your organization.
FAQs







Leave a Reply.