Samsung Knox vs. Android Enterprise: Do You Need Both? [2026 Comparison]
Introduction: Beyond the Buzzwords
In the 2026 enterprise mobile security market, Samsung Knox and Android Enterprise (AE) are not competitors; rather, they are core partners in building a “baseline compliance + deep protection” framework.
With industry developments such as strengthened app signature controls in Android 16 QPR and frequent high-risk vulnerabilities in MediaTek chipsets, relying solely on software-level defenses is no longer sufficient to counter complex threats—making the synergistic value of the two platforms increasingly critical.
The "Collaboration" Strategy

The essence of the collaboration between Knox and Android Enterprise (AE) is “Google sets the stage, Samsung performs”: Google establishes enterprise-grade management standards for Android devices through AE, covering foundational capabilities such as work profile isolation and silent app installation; Samsung, leveraging Knox, provides hardware-level security enhancements.
For example, Knox Mobile Enrollment (KME) supports AE’s device owner enrollment mode, enabling large-scale device initialization with just a network connection. This division of labor allows enterprises to achieve cross-brand management consistency while obtaining hardware-level protection on Samsung devices.
Evolution of Defense-Grade Security
The security evolution in 2026 shows two major trends:
- 1. AE is upgrading from “functional compliance” to “ecosystem security”, enforcing developer identity verification to block malicious software entry points.
- 2. Knox is extending from “device protection” to “end-to-end trust”, expanding Knox Vault technology to IoT endpoints.
Together, these developments address regulatory demands for “technology-sensitive priority” scrutiny—as highlighted by the HieFo case, any device involving core technologies now requires a hardware-backed security foundation.
1The Architecture of Trust: Understanding the "Fortress"
Hardware Root of Trust
The hardware Root of Trust is the core differentiator that sets Knox apart from AE. Samsung embeds an immutable cryptographic chip in the SoCs of the Galaxy S26 series and high-end A series devices, injecting a unique identity key at the manufacturing stage.
During device boot, this chip verifies the integrity of firmware, kernel, and system layers step by step—any tampering triggers a boot failure. In contrast, AE lacks a hardware-backed root of trust; its security relies solely on software integrity, making it vulnerable to physical tampering and chip-level attacks.
Samsung TEE vs. Knox Vault
TEE (Trusted Execution Environment)
The TEE (Trusted Execution Environment) is a logically isolated space based on ARM TrustZone technology. As a shared security component between Knox and AE, it handles sensitive operations such as biometric processing and payment encryption.
Within the AE framework, the TEE ensures the security of keys in work profiles; Knox further strengthens the TEE’s independence by physically isolating it from the main system. Even if the Android system is compromised, authentication data within the TEE remains protected from theft.
Knox Vault (Physical Safe)
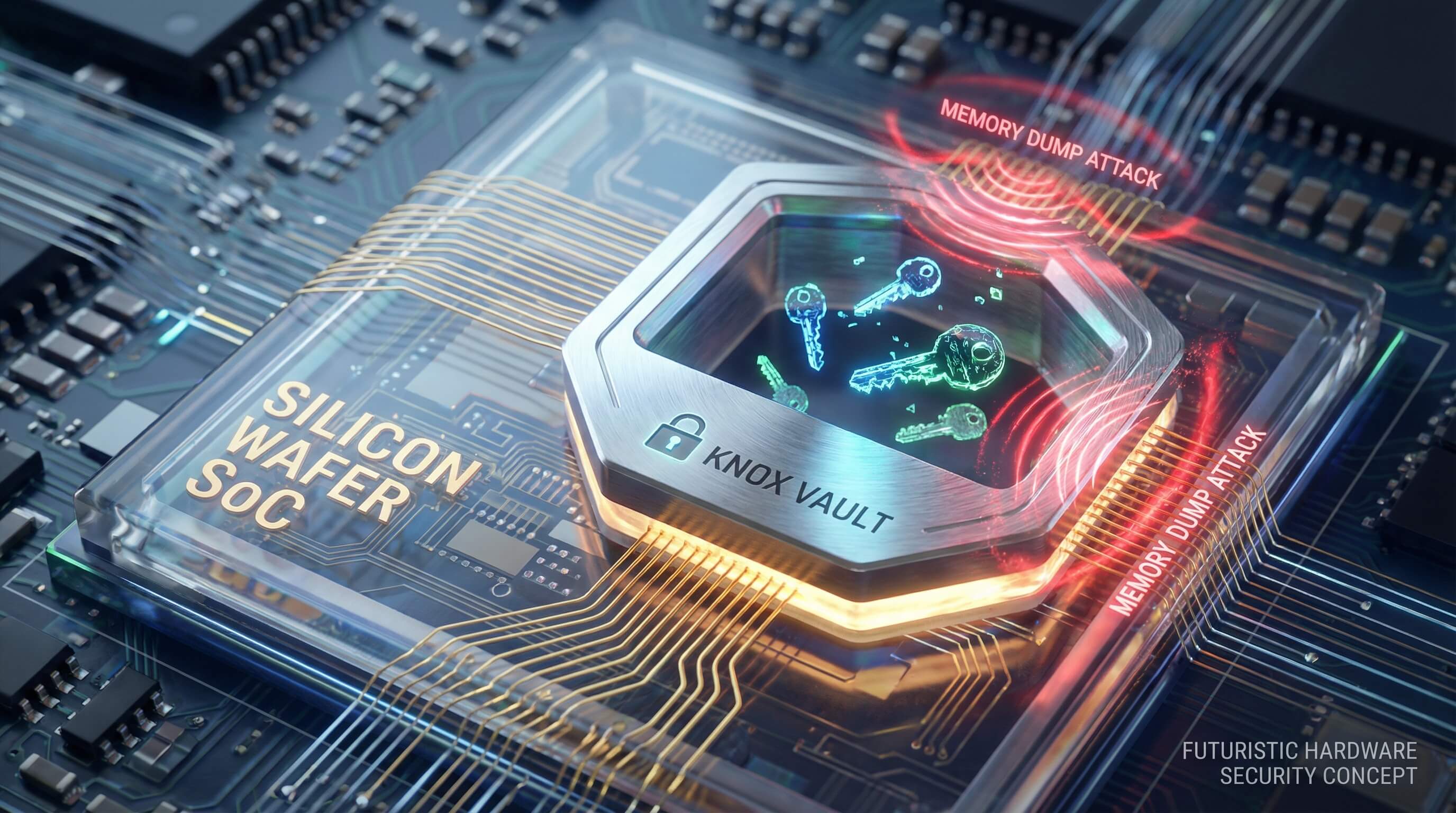
Knox Vault is the “ultimate defense” of Samsung’s 2026 security architecture, effectively serving as an on-device physical safe:
- Encased in titanium alloy, the independent storage chip has no direct circuit connection to the main SoC.
- Equipped with an independent power source, it can maintain 24-hour data encryption even if the main battery is removed.
- Supports distributed storage of sensitive data, with encryption keys split across three physical blocks.
In contrast, AE lacks hardware-level storage protection; sensitive data still relies on software encryption and remains vulnerable to memory dump attacks.
Real-time Kernel Protection (RKP)

RKP (Real-time Kernel Protection) is Knox’s core defense mechanism against kernel-level attacks, implemented through three key technologies:
- Real-time verification: Scans the kernel image every 50 milliseconds, triggering an immediate reboot if tampering is detected.
- Permission fuse: Intercepts high-risk operations, such as modifications to SELinux policies, and validates permissions in conjunction with Knox Vault.
- Vulnerability immunity: Preemptively blocks memory overflow attack vectors, such as those disclosed in MediaTek 2026 modem vulnerabilities.
In contrast, AE lacks a comparable mechanism and relies on vendor-pushed system patches, leaving a protection gap that can last days to weeks.
2Deep Dive Comparison: Samsung Knox vs. Android Enterprise
Baseline vs. Advanced Layer
Management Granularity
AE provides standardized management capabilities, while Knox delivers “hardware-level fine-grained control”:
- AE management boundaries: Work profile isolation, app whitelisting/blacklisting, basic device restrictions (e.g., disabling Bluetooth)
- Knox extended capabilities: Using OEMConfig (KSP) to control physical camera switches, disable USB debugging ports, and restrict firmware update channels
Example: Devices used by a central enterprise’s procurement staff can have cameras and USB ports disabled via Knox, while AE enables silent installation of work applications—ensuring both compliance and management efficiency.
The Enrollment Battle

In large-scale device enrollment scenarios, the differences between the two are significant:
- AE Enrollment: Zero Touch relies on Google services; NFC/ADB is only suitable for small-scale deployments and requires device-by-device operations.
- Knox Enrollment Advantages: KME (Knox Mobile Enrollment) supports “out-of-the-box” enrollment. Samsung devices purchased in bulk can be pre-configured with security policies and automatically connect to the MDM upon boot, increasing enrollment efficiency by over 10×.
For the 2026 State-owned Assets Supervision and Administration Commission (SASAC) Order No. 46 requirement of “full device lifecycle traceability”, KME’s enrollment logs can serve directly as compliance evidence.
3The "Kill Switch": The Knox Warranty Bit (e-Fuse)
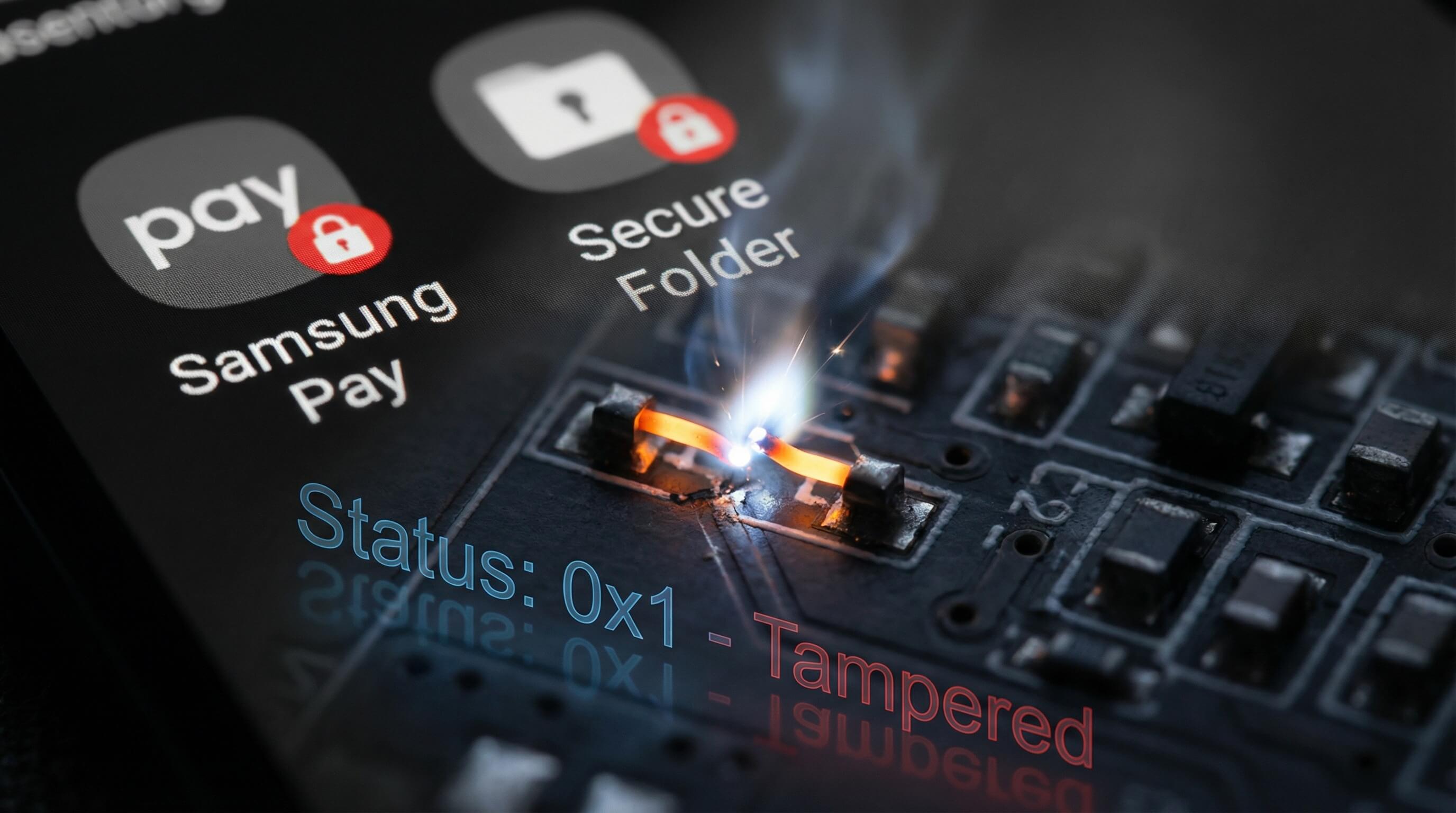
e-Fuse is Knox’s hardware-level “fuse mechanism”. When a device undergoes tampering actions such as rooting or bootloader unlocking:
- The hardware fuse irreversibly blows, permanently marking the Knox status as “tampered”.
- Core features like Secure Folder and Knox Vault are immediately disabled.
- The device loses official warranty and security update support.
This mechanism physically prevents attackers from bypassing security policies via root, whereas AE has no comparable hardware restriction—after rooting, functionality can only be limited through software measures.
What Happens if You Root?
e-Fuse is Knox’s hardware-level “fuse mechanism.” When a device undergoes tampering actions such as rooting or bootloader unlocking:
- The hardware fuse irreversibly blows, permanently marking the Knox status as “tampered.”
- Core features such as Secure Folder and Knox Vault are immediately disabled.
- The device loses official warranty and security update support.
This mechanism physically prevents attackers from bypassing security policies via root, whereas AE has no equivalent hardware restriction—after rooting, function can only be limited through software measures.
Impact on Enterprises
For enterprises, e-Fuse serves as a “touchstone” for compliance management:
- Risk Alert: MDM platforms can monitor the fuse status in real time; any tampering triggers immediate isolation, preventing sensitive data leakage.
- Accountability: Fuse blow records can serve as evidence of employee misconduct, meeting the SASAC Order No. 46 requirement of “whoever violates is accountable.”
- Cost Control: A financial institution monitored e-Fuse status and identified 12 tampered devices within six months, avoiding potential compliance fines exceeding 2 million RMB.
4AirDroid Business & Samsung Knox: Best Practices for Unified Management
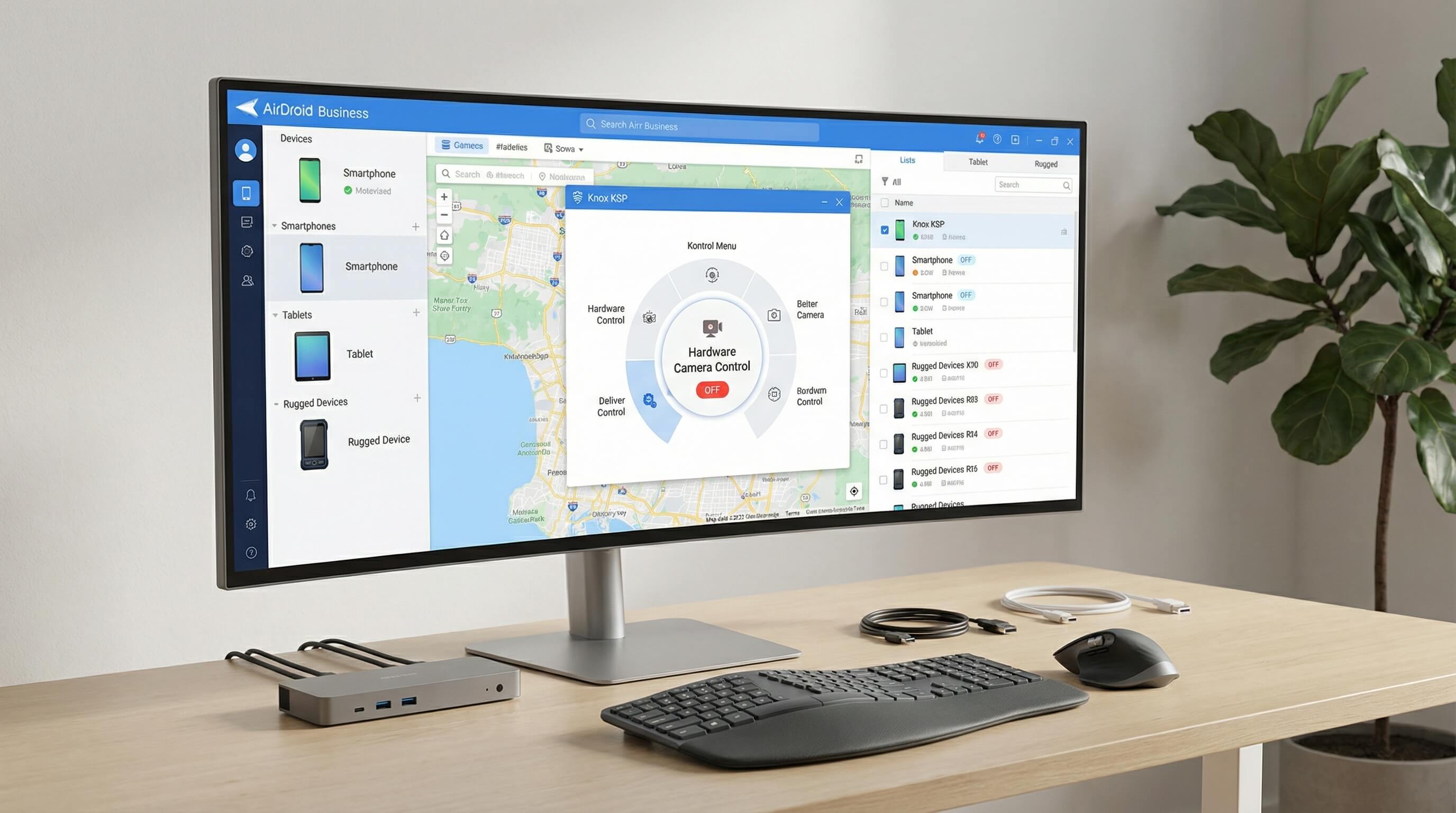
The Bridge: Samsung OEMConfig (KSP)
AirDroid Business, through deep integration with KSP (Knox Service Plugin), bridges Knox hardware capabilities with enterprise management workflows:
- Visual Knox policy configuration: One-click activation of Vault encryption and setting RKP protection levels.
- Integration with AE work profiles: Enables unified policy deployment combining hardware security + app management.
- Policy template reuse: Industry-specific templates for finance, healthcare, and other sectors can be directly adapted to regulatory requirements.
Strategic Compliance
For the 2026 cross-border regulations and state-owned enterprise compliance requirements, AirDroid provides three core capabilities:
- Compliance Dashboard: Real-time display of 12 security metrics, including Knox Vault activation rate and e-Fuse status, with automatic generation of CFIUS compliance reports.
- Operation Traceability: Remote operation logs are synchronized and stored in Knox Vault, meeting the requirement for full traceability.
- Risk Alerts: When a device deviates from the security baseline (e.g., fuse blown), alerts are immediately sent to administrators, triggering isolation procedures.
Remote Support on Secured Devices
Under Knox’s security restrictions, AirDroid enables “zero touch IT operations”:
- Encrypted remote debugging: All operation commands are transmitted through a Knox-certified encrypted channel and validated using Vault keys.
- One-time permissions: Third-party maintenance personnel receive temporary access, which is automatically revoked after use.
- Unattended device support: For devices like retail kiosks, IT can remotely reboot into safe mode to troubleshoot issues without disrupting local business operations.
5FAQs
Do I need both AE and Knox?
Depending on the scenario:
- Standard enterprises (non-sensitive industries): AE work profiles + basic management controls are sufficient.
- Sensitive industries (finance, government, defense): Both are required—AE provides the management foundation, while Knox delivers hardware-level protection, meeting regulatory requirements for “technology sensitivity.”
- Mixed device fleets: Non-Samsung devices are managed via AE, while Samsung devices receive enhanced security through Knox.
Does Knox cost extra?
Adopt a tiered pricing model:
- Knox Core (Basic Features): Pre-installed for free on all modern Galaxy devices; includes TEE and basic encryption.
- Knox Suite Essentials (Enterprise Base Edition): $30/device/year; includes KME and app management.
- Knox Suite Premium (Advanced Edition): Custom pricing; includes deep Vault management and zero-day vulnerability support.
- AE features: Completely free, but require an MDM platform (e.g., AirDroid) for management.
Can I manage non-Samsung devices alongside Knox?
Yes. AirDroid Business enables unified management of mixed device fleets:
- Samsung devices: Manage both AE work profiles and Knox hardware security policies simultaneously.
- Other Android devices: Only AE framework management features are enabled (e.g., app control, data isolation).
- iOS devices: Integrated via Apple Business Manager, creating a closed-loop cross-platform management system.
Conclusion: Build with AE, Fortify with Knox, Manage with AirDroid
6Final Verdict
In 2026, enterprise mobile security has entered a new era of “hardware foundation + software control”:
- Android Enterprise serves as the “universal language” for cross-brand management, addressing basic compliance and productivity needs.
- Samsung Knox acts as the “security armor” for sensitive scenarios, leveraging a hardware root of trust to defend against advanced threats.
- AirDroid Business functions as the “operational hub”, bridging the two to achieve a balance of security and efficiency.
For enterprises pursuing compliance and security, the combination of all three represents the irreplaceable optimal solution.
CTA: Start your 14-day free trial of AirDroid Business today and unlock the full potential of your Samsung device fleet.







Leave a Reply.