Compliance and Hotspot Control: Bridging the Gap Between Regulations and Device Behavior
With increasingly stringent global data regulations such as the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and the Payment Card Industry Data Security Standard (PCI-DSS), corporate compliance has shifted from "document-level formalism" to "practical implementation at the device level through mechanisms such as Mandatory Access Control (MAC) and Identity-based permission control.
"Hotspot sharing functionality on enterprise devices (especially Android devices) is becoming a major area of compliance risk. Employees privately enabling hotspots could lead to the leakage of customer privacy data, medical records, and payment information through unencrypted channels, directly triggering regulatory penalties.
According to the 2024 Enterprise Mobile Device Compliance Report, 68% of compliance fines were related to "uncontrolled device network behavior," with hotspot abuse accounting for over 40%.
However, most enterprises face a core dilemma: regulatory requirements are often "general principles" (such as "ensuring controllable and traceable data transmission"), making it difficult to directly translate into specific operations on the device side.
At this point, enterprise user management (MDM) solutions (such as AirDroid Business) become a crucial link that can transform abstract compliance clauses into enforceable policies on the device, achieving a closed loop of "regulatory requirements → IT policies → device behavior," ensuring compliance is no longer just an abstract concept.
1Policy as the Engine: Translating Abstract Regulations into Enforced Actions
A bridge connecting regulations and end users
Global data regulations regarding device hotspot usage often prioritize "data security" as a core principle, but lack clear operational guidelines. For example:
- GDPR requires "appropriate technical measures to ensure the security of data transmission," but does not specify "how to restrict device hotspots".
- HIPAA stipulates that "patient data transmission must be fully encrypted and traceable," but does not define "whether hotspot usage is compliant".
- PCI-DSS emphasizes that "payment data must be transmitted through isolated channels," but does not mention "how to prevent non-isolated transmissions caused by hotspots."
The core value of IT strategy lies in translating these fundamental principles into actionable device management rules. For example:
- Transforming "data transmission security" into "all enterprise devices are disabled for hotspots by default, only allowing access to pre-approved enterprise Wi-Fi".
- Transforming "transmission traceability" into "every hotspot activation operation must record the operator, time, and device information," creating Mobile device compliance evidence that stands up to audits.
- Transforming "payment data isolation" into "POS terminals are permanently disabled for hotspots, and USB ports are only used for charging".
A cross-border e-commerce company's IT team faced compliance risks due to a "lack of strategy": unclear rules regarding tablet hotspot usage led to employees turning on their hotspots for work convenience, resulting in customer order data being transmitted over public networks.
This prompted a GDPR audit requiring rectification. Subsequently, the team implemented a "hotspot disabling + trusted network whitelist" strategy using MDM (Management Management System), successfully passing a re-audit six months later and avoiding a potential €2 million fine.
Turn Regulations into Enforceable Device Policies with AirDroid Business
Bridge GDPR, HIPAA, and PCI-DSS from principles to device behavior. AirDroid Business converts compliance mandates into default hotspot disablement, trusted network whitelists, and identity-bound permissions—so every Android device does the right thing by design.
The role of MDM: From "passive advice" to "active defense."
IT strategies alone are insufficient to guarantee compliance if employees don't follow them and devices don't cooperate; the strategies will remain mere "paper rules." The core role of MDM is to ensure that strategies are "hard-hit," forcing all devices to comply with the rules through automated configuration and real-time monitoring, without relying on employee self-discipline, achieving Data security policy enforcement.
(Automated Configuration Deployment)
In the traditional model, IT teams need to manually configure hotspot permissions and network rules for each device, which is not only inefficient but also prone to "configuration omissions" (such as field devices not disabling hotspots). MDM (such as AirDroid Business) supports "batch automated configuration," transforming IT policies into default settings on the device side through Granular device permission management.
Hotspot disabled by default:
When a new device joins the network, AirDroid Business automatically disables the hotspot function, regardless of whether employees want to enable it.
Trusted network whitelist:
SSIDs and encryption information of corporate Wi-Fi and compliant VPNs are pre-imported, allowing devices to connect only to whitelisted networks and automatically rejecting untrusted channels such as hotspots and public Wi-Fi.
Policy group deployment:
Policies are pushed to groups based on device usage and department, for example, permanently disabling hotspots for the "Retail POS Terminal Group," while allowing the "Field Tablet Group" to apply for temporary hotspot permissions, avoiding a "one-size-fits-all" approach that impacts business operations.
A chain retail enterprise has 800 POS terminals. In the past, manually configuring hotspot disabling took three IT staff members two weeks, and store employees often modified the settings without authorization. By using AirDroid Business to batch distribute the "hotspot disabling" configuration, the deployment of all devices was completed in one hour, and the configuration could not be manually tampered with by employees. The hotspot violation rate dropped from 35% to 0, demonstrating hotspot sharing accountability at scale.
Real-time status monitoring and correction

During use, devices may deviate from compliance due to system updates, employee actions, etc. (e.g., employees bypassing hotspot restrictions using third-party tools). MDM's real-time monitoring and correction functions can promptly detect and block violations, ensuring devices remain on track and preserve Compliance audit trail integrity:
Real-time Status Monitoring:
AirDroid Business's dashboard provides real-time monitoring of all devices' hotspot status (enabled/disabled) and network connection type (corporate Wi-Fi/hotspot/public network). IT teams can grasp the overall compliance situation without needing to check each device individually.
Automatic Violation Correction:
If a device violation is detected (e.g., enabling a hotspot through technical means or connecting to an unauthorized network), the system will automatically execute preset actions such as immediately disabling the hotspot, disconnecting from untrusted networks, and sending an alert to the IT team.
Abnormal Behavior Tracing:
For violating devices, their historical operation records can be traced back (e.g., "when did they attempt to enable a hotspot?" "Were restrictions successfully bypassed?") to analyze the reasons for the violation and optimize strategies.
A healthcare company's nursing tablets experienced an issue where employees were "breaking hotspot restrictions": nurses, to facilitate the transfer of patient data, enabled hotspots via third-party software, potentially exposing medical records. AirDroid Business detected the abnormal hotspot status, immediately disabled it automatically, and sent an alert to the IT team.
Subsequently, the IT team traced the installation path of the bypassing tool through logs, supplemented their "application blacklist/whitelist" policy, and completely prevented similar risks.
Automated Enforcement and Live Violation Blocking
Stop configuration drift and hotspot abuse in real time. With batch policy deployment, continuous status checks, automatic hotspot shutdowns, and instant alerts, AirDroid Business keeps devices compliant—without relying on employee self-discipline.
2Identity as the Perimeter: Granular Hotspot Authorization via User Management
Another core requirement for compliance is "traceability of responsibility" in the event of a data breach related to a hotspot. Companies must clearly identify "who operated the device" and "who turned on the hotspot," otherwise they will face compliance penalties due to "unclear responsibility.
"MDM achieves a strong binding between hotspot permissions and user identities through user identity management, ensuring that 'only the right people can use the hotspot' and holding them accountable for every operation, an approach aligned with the principle of least privilege mobile device logic.
Solving the problem of "who" is sharing data
In traditional device management models, hotspot usage often faces the dilemma of unclear responsibilities: a single tablet may be shared by multiple employees, making it impossible to trace the specific operator after the hotspot is activated; after an employee leaves, hotspot permissions are not promptly revoked, leading to device misuse by others. These issues can all become points of contention in compliance audits.
MDM's user management functions (such as AirDroid Business's "Member Management" module) solve the core problem of "who is using the hotspot" through a triple binding of "device - user - permission":
One person, one account:
Each employee has an independent MDM account, only able to operate company devices under their own name, avoiding the ambiguity of responsibility caused by "multiple people sharing one device.";
Permissions follow the person:
Hotspot permissions are linked to employee identity. For example, field engineers have "temporary hotspot application rights," while office staff do not. When an employee leaves, their account is canceled, and permissions are automatically revoked.
Operation logs:
Every hotspot activation, permission application, and network switching operation is recorded in the "operation log," marking the operator's account, ensuring that "every action is accountable."
A logistics company was embroiled in a compliance dispute due to "unlinked driver identities": Field tablets were not associated with specific drivers, and when a driver used a hotspot to transmit route data, customer information was leaked. During the audit, the responsible party could not be identified, and the company was ordered to pay 500,000 yuan in rectification fees.
After introducing AirDroid Business, the company assigned a dedicated account to each driver, linking tablet operations to driver identities. Even if problems arise later, the responsible party can be located within 10 minutes, improving compliance traceability efficiency by 90%.
Implementing the Principle of Least Privilege
One of the key principles of compliance management is "least privilege," granting employees only the necessary permissions to complete their work, and avoiding granting excessive permissions to reduce risks at the source. MDM achieves "on-demand allocation" of frequently used permissions through granular user grouping and permission configuration, avoiding "one-size-fits-all" or "over-authorization".
Role-based access control
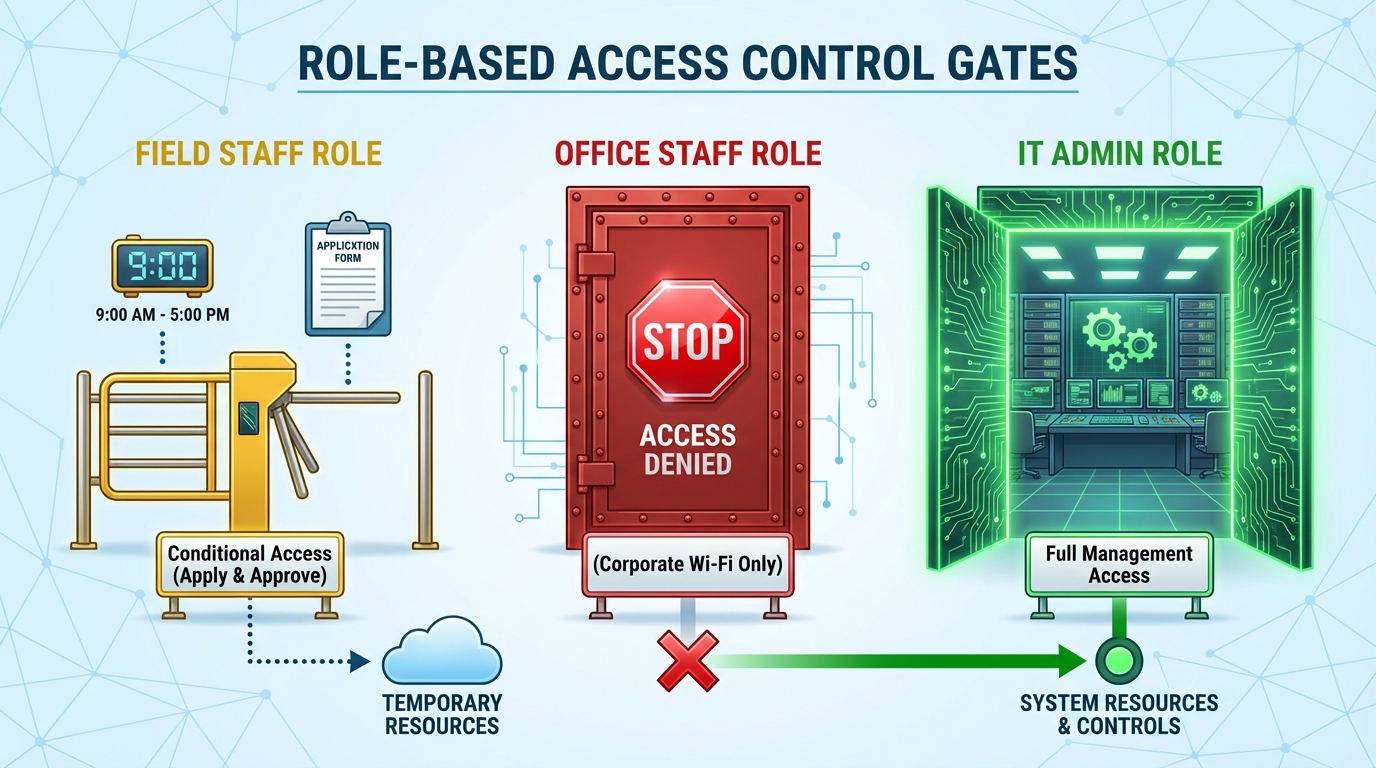
Employees in different roles have different hotspot needs: field staff may need to temporarily enable hotspots to synchronize data, while front desk staff have no hotspot permissions at all. MDM supports dividing hotspot permissions by "role" for granular control:
Administrator role:
The IT team has "hotspot permission configuration rights," allowing them to enable/disable device hotspots in batches and view all operation logs.
Field staff roles:
Such as logistics drivers and field engineers have "temporary hotspot application rights"; they need to submit the usage scenario (e.g., "remote area without Wi-Fi") and duration (e.g., "2 hours"), and permissions take effect after IT approval.
Office staff roles:
Such as office clerks and cashiers have no hotspot permissions by default, and are only allowed to access the company Wi-Fi to avoid unnecessary risks.
A construction company configured RBAC permissions through AirDroid Business: granting "hotspot application rights" only to project team engineers, while employees in other departments had no access. After implementation, the frequency of hotspot usage decreased from 120 times per month to 35 times, all of which were compliant work scenarios, significantly reducing the risk of data leakage and avoiding unnecessary traffic consumption.
Attribution of responsibility and binding of identity
Compliance audits not only require "device compliance" but also "behavior traceability." If hotspot usage leads to data breaches, companies must provide evidence of "who operated, when they operated, and what they operated," otherwise they will be deemed to have "failed to fulfill their management responsibilities."
MDM achieves traceability of responsibility through a strong binding of "identity - operation - logs":
Operation logs are linked to identity:
Every hotspot activation/deactivation, permission application/approval operation records the operator's account, name, and department, not just the device ID.
Timestamps are tamper-proof:
Every record in the log has a timestamp accurate to the second and is stored in an encrypted format, making it impossible to manually modify or delete, ensuring the authenticity of the evidence.
Multi-dimensional search:
Supports searching logs by "operator, time, device model, behavior type," such as "check if employee A turned on the tablet hotspot on October 20th," with results found within 10 seconds.
3Irrefutable Chain of Evidence: Compliance Auditing and Due Diligence

Audit Log: The "Black Box" of Compliance Review
When facing annual audits from regulatory agencies or emergency investigations following data breaches, the worst scenario for businesses is having "no evidence to back up their claims." In these situations, the audit logs provided by MDM act as a "black box," offering legally valid electronic evidence.
Full-dimensional behavior recording
A sound compliance audit system needs to answer three core questions:
1. Logging Critical Actions:
AirDroid Business's auditing system comprehensively records all dimensions of information related to hotspots:
Timestamp:
The operation time is accurate to the second.
User ID:
Which administrator issued the policy, or which user enabled the feature?
Device ID:
Which device performed the operation.
Behavioral Details:
Hotspot duration, data usage, etc.
2. Proving Due Diligence
From a legal perspective, there is a fundamental difference between being hacked and a breach caused by negligence. The greatest value of audit logs lies in proving a company's due diligence.
By demonstrating detailed policy implementation and blocking records, companies can prove to regulators: "We have established rigorous policies, deployed effective tools, and intercepted violations in real time." This complete chain of evidence is a solid shield for companies to protect themselves in compliance storms.
Compliance-Ready Audit Trail for Hotspot Usage
Produce immutable, identity-linked evidence for every hotspot operation—who, when, which device, and what action. Export audit-friendly logs to substantiate due diligence and pass GDPR, HIPAA, and PCI-DSS reviews with confidence.







Leave a Reply.