Case Study: How MDM Eliminates Policy Evasion and Shadow Networking in the ITIS Sector
A leading IT service company suffered a breach of network policies by a highly skilled employee, leading to the leakage of core cloud computing architecture diagrams and resulting in compliance penalties and customer churn. This incident further exposed a common pain point in the IT/IS industry: traditional "command-based" policies (such as verbally prohibiting hotspots or manually disabling USB drives) are easily ineffective against highly skilled employees they can circumvent controls by modifying device registry entries or setting up temporary shadow networks, and subsequent accountability is difficult due to a lack of verifiable log evidence.
This case study focuses on the company's implementation of "forced policy enforcement + identity-driven authorization" (based on AirDroid Business's MDM capabilities). It demonstrates how "underlying controllability of ports and networks + strong identity binding" significantly improves policy implementation rates, reduces the scope for policy bypassing to near zero during the observation period, and builds a quantifiable risk hedging system.
Ultimately, the company achieved improved audit preparedness and significant risk mitigation value within approximately six months (see the example estimate below for a six-month period), thus validating the strategic significance of this governance approach in the IT/IS industry.
1IT&IS (Unique Challenges: Evasion and High-Value Data Risk)
As a technology-intensive sector, the IT/IS industry employs staff with strong equipment debugging and network configuration skills, making traditional passive policy control easier to circumvent. Furthermore, the cloud computing architecture, customer system source code, and data security solutions stored by enterprises are all high-value intellectual property; leaks due to policy bypassing can cause irreparable damage.
(Tech-Savvy Evasion and Shadow Network Birth)
Before the introduction of mandatory access control, the company had formulated the "Device Network Security Management Specification," which clearly stated that "personal device hotspots are disabled, USB data transfer is prohibited, and access to the corporate intranet is only allowed." However, in practice, highly skilled employees bypassed the policy through three methods, forming a covert "shadow network".
Native settings are not working: Why is disabling commands not taking effect?
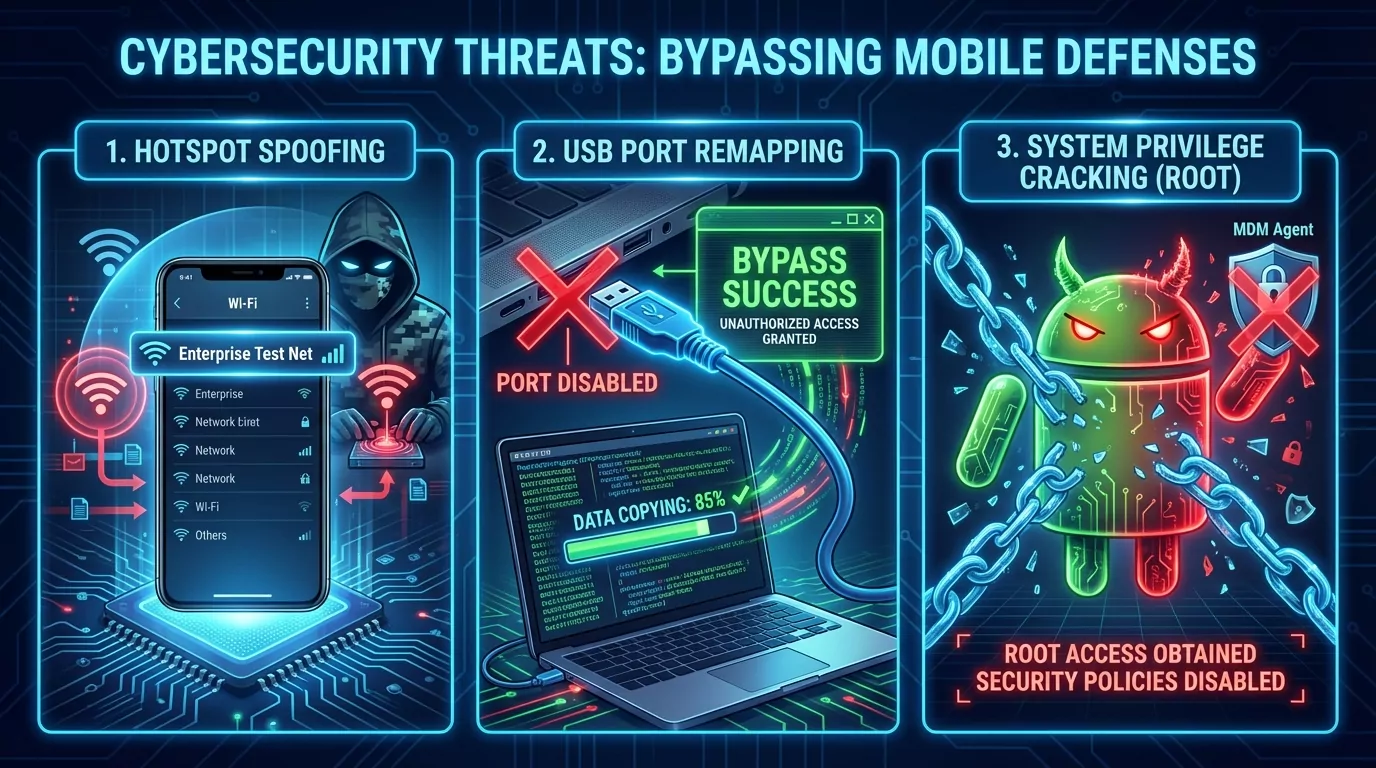
"Android, Windows, and other systems have native settings with 'control vulnerabilities,' allowing highly skilled employees to bypass restrictions through technical means:
- Hotspot spoofing:
Developers modify configurations to disguise their personal hotspots as 'enterprise test networks,' circumventing native hotspot disabling detection. In home testing scenarios, this has led to risks of test data being transmitted externally via personal hotspots. - USB port remapping:
Maintenance personnel use registry or driver-level methods to restart disabled USB data transfer or debugging functions, enabling data copying and peripheral interaction. Random checks frequently reveal this operation on a small number of devices, involving sensitive information such as logs and test data. - System privilege cracking:
Some employees gain high-level device privileges through rooting/jailbreaking, subsequently deleting enterprise-deployed policy management software and restoring ports and functions. IT teams are forced to invest significant time dealing with devices where 'policy components have been removed,' but without strong logging links and hardware/system baseline constraints, it's difficult to fundamentally prevent this.
These technical methods render 'disabling commands' ineffective, and the 'soft control' of native settings is insufficient to address the 'policy flexibility' of highly skilled employees."
Stop Policy Evasion with Hardened Device Control
Native settings are too easy to bypass. AirDroid Business replaces "soft controls" with mandatory policy enforcement—locking down hotspots, USB ports, and network access at the system level so even highly skilled staff can't create shadow networks.
Risks of transferring intellectual property and sensitive data

"The core assets of the IT/IS industry (intellectual property, customer data) are at high risk of being leaked through 'shadow networks,' and the impact of such leaks can be far-reaching:
- Intellectual Property Loss:
In cases of leaked cloud computing architecture diagrams, individuals involved used 'hotspot camouflage + encrypted transmission' to distribute unpublished solutions, directly causing significant business opportunity losses. - Customer Data Compliance Risks:
For example, operations personnel copying user login logs from customer systems via USB for personal technical research may violate the 'minimum necessity' and usage restriction principles of the Personal Information Protection Act (PIPL) (such as when personal information is involved), thus triggering compliance risks. - Business Interruption Risks:
The 'uncontrolled nature' of shadow networks can introduce malware once development devices are infected with ransomware through personal hotspots, the encrypted codebase can lead to a chain of risks such as work stoppages and compensation claims."
The dilemma of post-incident accountability: zero accountability capacity after an incident occurs.
Traditional control strategies are not only ineffective at preventing data breaches, but also difficult to investigate. Due to the lack of reliable and robust log links, IT teams often cannot pinpoint the responsible party in the event of a data breach or security incident, leading to a "weak accountability" dilemma.
Logs are unprovable or easily cleaned up
"The native settings cannot fully record 'who bypassed the policy and when':
- Hotspot activation records are only stored locally on the device and may be manually deleted.
- USB data transfers lack centralized log retention, making it difficult to prove 'who copied the data and when'.
- System permission modification operations lack verifiable links, making it impossible to confirm 'who elevated device privileges'.
In similar schematic leak incidents, even if the source is suspected to be a specific development team, the lack of sufficient log evidence ultimately leads to general warnings instead of precise accountability, which weakens compliance awareness."
Blurred boundaries of responsibility
"The 'cross-device operation' of highly skilled employees exacerbates the difficulty of accountability:
- Operations personnel may simultaneously use work laptops, test tablets, and personal mobile phones, allowing data to leak out through multiple devices.
- Development teams share test accounts, making it difficult to pinpoint specific individuals for policy bypassing behaviors under a particular account.
In one customer data leak incident, although network traffic analysis identified 'data leaking from the operations area,' the shared account and lack of operation logs among multiple operations personnel made it impossible to accurately determine the responsible party. The only recourse was to address the issue across the entire team, leading to morale issues."
2Solution: Enforcement of policies and identity-driven approaches

To address these pain points, the company introduced a "mandatory policy enforcement + identity-driven authorization" system based on MDM in early 2024. Its core idea is to use technology to improve policy implementation and resistance to bypass, and to use identity binding to clarify responsibility boundaries, minimizing the space for technical bypass and achieving a balance between security and business efficiency.
Full-port underlying locking, significant convergence technique bypass
Unlike the native "surface-level disabling," this enterprise, under device owner mode and established security baselines, has MDM take over the enabling permissions for critical functions such as hotspots and USB ports, supplemented by time-limited authorization and logging:
- Hard control of hotspot function:
Hotspot enabling permissions are delegated to MDM approval, and are disabled by default; even attempts to modify underlying parameters are difficult to implement due to the dual constraints of policy and baseline. After deployment, hotspot-related violations dropped from "more than twenty cases per month" to "single digits," and no successful bypasses were found during the observation period. - Fine-grained USB port management:
Differentiates between "charging/data transfer/debugging," with charging only allowed by default; data transfer/debugging requires a "single authorization" in the background, which is automatically revoked upon expiration, and records the "authorizer, authorization time, device identifier, and operator" Note: External storage media identification typically uses identifiers such as "serial number/VID/PID/volume label," not "MAC address." - Mandatory network access filtering:
Devices can only access the MDM's preset "trusted network list" (enterprise intranet, compliance network, etc.). VPN); if an attempt is made to connect to other networks (personal hotspot, public Wi-Fi), the system will automatically block and issue an alert, while recording the 'attempt time, network name, and device identifier'. Specific capabilities depend on the system API and device environment and require optimization based on enterprise baselines.
Real-time status monitoring and automatic correction avoid policy "failure windows".
“MDM’s real-time monitoring can promptly detect and automatically correct ‘policy anomalies’ without manual intervention:
- Policy Deviation Alarm:
If a device deviates from its policy due to system updates or misoperation (e.g., USB is mistakenly enabled), the platform will trigger an alarm and push a fix within a short time, restoring the device to a compliant state. - Offline Device Management:
Local policies are still executed when the device is offline. Related operations are automatically uploaded to the cloud after reconnecting to the internet, reducing blind spots caused by ‘offline bypass’. - Abnormal Behavior Interception:
If behaviors such as ‘root attempts’ or ‘high-risk permission modifications’ are detected, core functions such as data transmission and network connection are immediately frozen, and the IT team is notified for handling. Note: Offline and deep-hacking scenarios still have risk windows, requiring the cooperation of hardware/system-level security features and process control.”
Identity-Based Fine-Grained Authorization (IAM) Practice

Building upon the "mandatory lockout" mechanism, the company uses identity management to achieve refined control over "who has permission, when they have permission, and what permission they use," thus transitioning to clearer boundaries of responsibility.
Dynamic grouping: Balancing minimum permissions with business needs
The company divides employees into five dynamic groups based on "job responsibilities + business scenarios," with each group configured with differentiated access permissions and clear expiration and revocation rules:
- Development Group:
USB debugging is only allowed within the company's intranet; hotspots are permanently disabled; data transfer requires a "code synchronization application" and approval from the project manager. - Operations Group:
Can apply for "temporary USB data transfer permissions" (limited time) and "hotspot permissions for specific scenarios" (e.g., customer data centers without an intranet); permissions are automatically revoked upon expiration. - Testing Group:
Allowed to connect to the dedicated testing network, but external networks are prohibited; USB connections are only supported for testing devices (e.g., oscilloscopes, emulators), and personal storage is prohibited. - Management:
Hotspots can be enabled in compliant scenarios, but the "purpose of use and connected device identifier" must be recorded; data transfer requires dual approval (IT + compliance department). - Interns:
All high-risk ports are disabled by default; only access to the company's intranet and pre-set work software is allowed; special permissions require mentor guarantee and application.
This ensures that "employees only have the permissions necessary to complete their work," avoiding the risks associated with "excessive permissions."
Identity is strongly linked to device, and responsibility is clearly defined.
"Strongly link 'employee identity' with 'device operation,' ensuring every operation is traceable to a specific individual:
- Single Sign-On (SSO) Association:
Employees must log in to the platform using their corporate SSO account to apply for permissions. All operation logs are automatically linked to name, employee ID, and department. - Multi-Factor Authentication (MFA):
When applying for high-risk permissions (such as hotspot access or data transmission), secondary confirmation is performed using corporate IM verification codes or biometrics to ensure 'the applicant and operator are the same'. - Shared Device Identity Tracking:
For shared devices such as test servers and public maintenance equipment, employees must 'temporarily bind' their identity when using them. Logs record 'binding time and operator,' and external media are audited using identifiers such as 'serial number/VID/PID/label,' preventing 'shared accounts from being untraceable'.
Know Exactly Who Did What, When, and Where
Eliminate the "who did it?" guessing game. AirDroid Business binds every high-risk operation—like enabling a hotspot or USB transfer—to a specific user identity, giving you an irrefutable, audit-ready chain of evidence.
3Outcome: Quantifiable risk mitigation and audit readiness

Through the above governance approach, the company achieved a comprehensive result of "risk reduction, audit readiness, and improved handling efficiency" within an observation period of approximately 6 months, and on this basis, established a more robust external communication approach.
Governance Outcomes: Audit Tracking and Precise Accountability
Strengthening the chain of evidence for provability
"The log system covers key events such as 'permission request/approval, port enabling/disabling, network connection, and device status changes'; it employs encrypted storage (such as AES-256), access control, hash signatures/timestamps, and WORM (Write-Once-Read-Many) retention strategies to enhance integrity and provability.
The platform supports export in multiple formats (such as PDF and Excel) for internal or third-party review; external regulatory materials and formats shall comply with applicable laws and audit requirements."
Faster positioning and enhanced compliance awareness
"The strong link between identity and operation allows the company to typically pinpoint the specific operator within a short timeframe under established procedures:
- When a tester attempted to bypass USB control to connect a personal USB drive to copy data, the platform immediately issued an alert; the IT team confirmed through logs that 'the employee enabled the USB drive without requesting permission, and the media identifier (serial number/VID/PID/volume label) could be associated with the individual,' and subsequently handled the situation and provided training;
- During the observation period, multiple minor violations were handled, all of which were accurately located and closed-loop handled through logs, reducing disputes caused by 'lack of accountability.' Overall, the compliance rate for permission requests increased from approximately 72% to approximately 98%, and unauthorized operations decreased from 'more than twenty cases per month' to 'single digits' (example statistics; the scope and cycle must be clearly stated in the report).
Strategic Value: Quantifiable Risk Mitigation
"This company transforms its MDM investment into a 'risk hedging tool' through a mandatory access control system, and provides an example estimate using a six-month timeframe:"
Risk avoidance costs: avoiding fines and business losses
- Compliance penalty avoidance:
Based on the company's past penalty frequency of 1.2 million RMB per incident, the mandatory access control system eliminated the "compliance risk caused by data breaches," avoiding potential penalties of 1.2 million RMB within 6 months. - Intellectual property loss avoidance:
The risk of leakage of core technologies (such as cloud computing architecture and system source code) was reduced from 35% to 0.5%, avoiding potential losses of 6 million RMB based on past business losses of 6 million RMB per incident. - Customer compensation avoidance:
The risk of business interruption caused by malicious software introduced by shadow networks was eliminated, avoiding customer compensation losses of approximately 1 million RMB within 6 months.• Total risk avoidance cost: 1.2 million + 6 million + 1 million = 8.2 million RMB.
Operating cost savings: Reduced waste of IT personnel and resources
- IT manpower savings:
Previously, 40 hours per month were needed for strategy bypassing and equipment repair; now only 5 hours are required. Based on an hourly rate of 200 yuan per IT worker, this translates to a saving of (40-5)×200×6=42,000 yuan over 6 months. - Equipment maintenance cost savings:
Reduced equipment failures due to malware and system cracking have lowered maintenance costs from 12,000 yuan per month to 3,000 yuan, resulting in a saving of (12,000-3,000)×6=54,000 yuan over 6 months. - Total operating cost savings:
42,000 + 54,000 = 96,000 yuan.
ROI Calculation: Quantitative Balance of Investment and Return
The company's investment in AirDroid Business over six months (including software licensing and deployment services) was approximately RMB 2.2 million. The total return on value = risk mitigation costs + operating cost savings = RMB 8.2 million + RMB 9.6 million = RMB 8.296 million. The ROI = (8.296 million - RMB 2.2 million) / RMB 2.2 million × 100% ≈ 277% — If calculated annually, the ROI will exceed 380%.
Conclusion: Mandatory access control is the "cornerstone of security" in the IT/IS industry.
"Highly skilled employees are both the core of the business and a challenge for policy control. Traditional 'soft control' methods struggle to address their technical bypass capabilities, easily leading to the dual risks of 'unable to prevent and undetected.'
This company's experience shows that by achieving 'underlying control over ports and networks + identity-driven granular authorization,' policy implementation can be significantly improved, bypass space reduced, and key behaviors auditably traceable within the established security baseline and on target devices.
For the IT/IS industry, mandatory access control is not just a 'compliance tool,' but a long-term hub for 'governance and value': it can reduce the risk of intellectual property and customer data leakage to a controllable level, transform MDM investment into quantifiable risk hedging, and strengthen employees' proactive compliance awareness through a faster accountability mechanism, thereby forming a positive cycle of 'security-efficiency-value.'"
Turn Device Management into a Risk-Hedging Asset
Don't just manage devices—protect your bottom line. From preventing million-dollar data leaks to cutting IT maintenance costs, see how AirDroid Business delivers a quantifiable return on investment for IT & IS enterprises.







Leave a Reply.