Stop Unauthorized Access: How Granular MDM User Roles Secure Your Enterprise Devices
Imagine a former employee accessing sensitive data on a company tablet, or a contractor with excessive privileges deleting critical files. These insider threats are real, as IBM reports that 23% of breaches arise from such issues. Gartner predicts that by 2025, half of cloud security incidents will result from poor IAM practices. Your device security relies on precise permissions—broad MDM policies create exploitable blind spots for both malicious actors and well-meaning staff. This underscores the necessity of robust MDM user management to ensure secure and efficient device access control.
1 What is MDM User Management?
MDM (Mobile Device Management) User Management is a feature within MDM solutions that allows organizations to control and manage user access and permissions for mobile devices deployed within their network. It provides a structured approach to assigning roles and permissions, ensuring that each user has access only to the features and data necessary for their role. Key aspects include:
- Role-Based Access Control (RBAC): Allows the creation of different user roles, such as administrators, managers, and standard users, each with specific permissions.
- Customizable Permissions: Enables detailed control over what each user can do, such as installing apps, accessing data, or changing settings.
- User and Device Grouping: Facilitates the organization of users and devices into groups for easier management and policy enforcement.
- Security and Compliance: Ensures that only authorized users can access sensitive data and perform critical operations, enhancing security and compliance with regulations.
- Audit and Monitoring: Tracks user actions and device activities to provide transparency and accountability.
MDM User Management helps streamline device management, improve security, and enhance operational efficiency by ensuring that users have appropriate access to resources.
2 Why MDM User Management is Important?
MDM User Management is crucial for several reasons:
- Security: It ensures that only authorized users have access to sensitive data and critical device functions, reducing the risk of data breaches and unauthorized access.
- Compliance: Helps organizations meet regulatory requirements by controlling who can access specific data and applications, and by maintaining detailed audit trails.
- Efficiency: Streamlines device management by allowing IT teams to assign roles and permissions efficiently, reducing the administrative burden and enabling quicker responses to issues.
- Customization: Offers flexibility to tailor access and permissions based on specific roles and responsibilities within the organization, ensuring that users have the tools they need without unnecessary access.
- Accountability: Provides visibility into user actions and device usage, facilitating monitoring and auditing to ensure compliance with internal policies and external regulations.
- Scalability: Supports the growth of an organization by allowing easy management of a large number of users and devices, adapting to changing needs and structures.
3 How AirDroid Business Delivers Granular Role-Based Management
AirDroid Business provides a comprehensive user management system that enables organizations to efficiently invite, assign roles, and manage team members, ensuring secure and organized access to company resources.
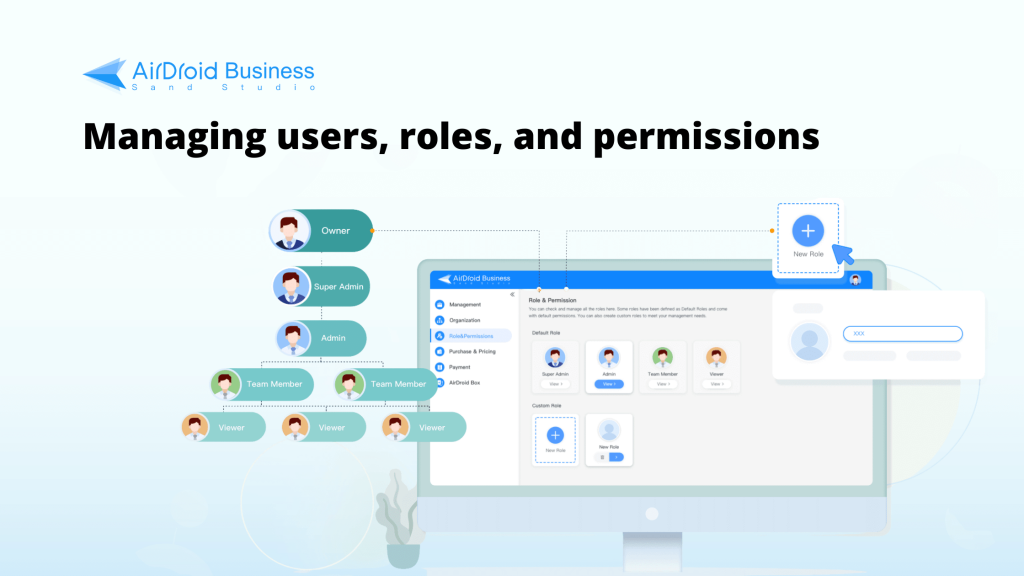
1Roles and Permission
Default Roles
AirDroid Business offers Default Roles to streamline the assignment of access rights:
- Owner: This role has comprehensive access to all features and system settings, including the ability to manage subscriptions and payments. The Owner holds the highest level of authority and can make critical decisions regarding user roles and permissions.
- Super Admin: Similar to the Owner, but without the ability to manage payment options. Can access all features and configure system settings and user permissions.
- Admin: Has access to most functions and data. Limitations include no access to specific settings like Device Map and Geofence.
- Team Member: Access to Remote Control and Device Monitoring features. Limited access to certain functions within the Device Dashboard and Workbench.
- Viewer: Can monitor devices remotely. No access to other functions or settings within the Admin Console.
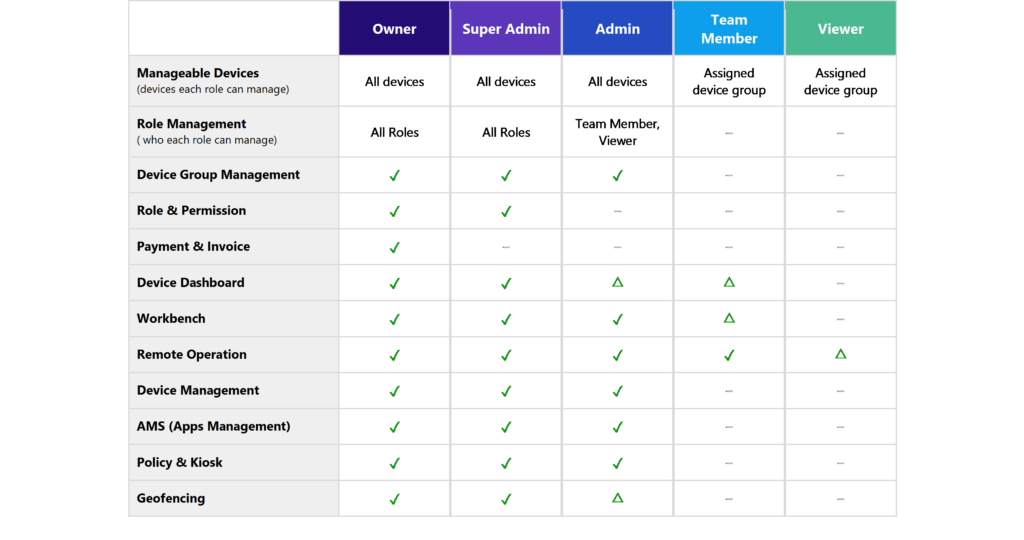
Note: There can only be one owner per AirDroid Business account, whereas you can have as many Super Admins, Admins, Team Members, or Viewers as you wish. See the table below for a complete list of all the permissions that are given to each role:
Custom Roles
Custom Roles provide flexibility beyond the default roles by allowing administrators to define specific permissions for each role. This means organizations can tailor access rights to align with various job functions, ensuring that employees have access only to the resources they need.
- Granular Control: You can specify which features and data each role can access, modify, or view. This ensures that sensitive information is only accessible to authorized personnel.
- Scalability: As businesses grow, custom roles can be adjusted or expanded to accommodate new job functions or organizational changes without disrupting existing workflows.
- Security: By limiting access to only necessary functions, custom roles help reduce the risk of data breaches and unauthorized access.
For example, a custom role for IT support staff might include permissions for remote device management and troubleshooting tools but restrict access to financial data or strategic settings.
2Account Activity Reports
AirDroid Business's Account Activity Reports feature provides organizations with comprehensive monitoring of user actions within the system, ensuring transparency and security in device management.
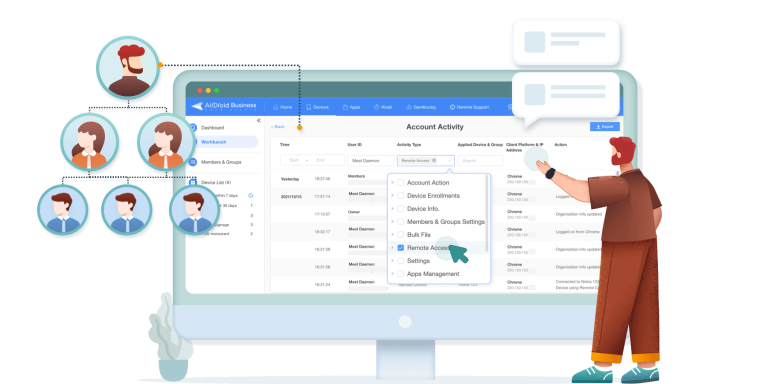
Feature Overview:
- Activity Monitoring: Tracks all account-related operations, including account behaviors, device registration history, settings changes, and app updates.
- User Behavior Analysis: Helps administrators track and analyze user activities within the system to identify abnormal behaviors or potential security risks.
- Historical Records: Provides detailed historical activity logs for auditing and compliance checks.
Use Cases:
- Data Anomaly Investigation: When unusual device data usage is detected, administrators can use account activity reports to trace user actions during the relevant period to identify the source of the issue.
- Permission Management: Monitors changes made by users to devices and system settings, ensuring that only authorized personnel perform critical operations.
- Security Audits: Regularly reviews user activities to identify and mitigate potential security threats.
The Account Activity Reports feature helps businesses effectively monitor user actions, enhancing the security and compliance of device management.
4 Case Studies of AirDroid Business MDM User Management
1Case 1: Retail Chain Group - Efficient Multi-Store Management

Company Overview
A rapidly expanding fresh produce supermarket chain with over 300 stores, providing fresh food and daily necessities. Each store is equipped with Android tablet POS systems and electronic shelf labels for handling payments, inventory monitoring, and member promotions.
Challenges
- Centralized Management Complexity: As the number of stores increased, the headquarters IT team struggled to monitor the status of each device in real-time, leading to delayed responses for device issues or application updates.
- Inflexible Permission Allocation: While managers wanted regional managers and store managers to handle some device issues directly, there was a risk of system crashes due to potential misuse.
- Data Security Pressure: Each tablet contains sales data and member information, posing risks if unauthorized access or accidental data deletion occurs.
Solution
Multi-Tier Role Configuration:
- Super Administrator (Headquarters IT): Holds the highest permissions for managing all devices, setting global security policies, and pushing application updates.
- Regional Administrator: Manages devices within their jurisdiction, capable of remote screen viewing and application restarts.
- Store Manager: Has basic operational permissions for their store's devices, such as checking device status and submitting logs, but cannot change security settings.
Device Group Management: Devices are grouped by region and store number, ensuring data is managed separately with no interference.
Real-Time Auditing and Security Monitoring: The system logs all administrator actions, allowing for immediate tracing and correction of any anomalies.
Results
- Smoother Store Operations: Regional administrators or store managers handle minor issues or updates promptly, enhancing efficiency.
- Data and Permission Security: Sensitive operations are restricted to headquarters IT, reducing the risk of unauthorized actions.
- Enhanced Operational Competitiveness: Clear roles and permissions support efficient store operations and improve customer experience during expansion.
2Case 2: Logistics Company - Large-Scale Vehicle Equipment Management

Company Overview
A national third-party logistics company with thousands of trucks and delivery vehicles, each equipped with an Android tablet for GPS tracking, documentation, order processing, and driver attendance management.
Challenges
- Driver Proficiency Issues: Drivers had varying levels of familiarity with device operations, leading to issues like accidental app deletions or system setting changes.
- Slow Response from Dispatch Center: Device issues needed to be reported to headquarters IT, delaying timely resolutions and affecting transport efficiency.
- Security and Compliance: High data security requirements for vehicle tracking, customer information, and order data.
- Frequent Updates: High-volume updates during peak seasons for transport scheduling and electronic signing apps posed management challenges.
Solution
Role Division and Permission Delegation:
- Super Administrator (Headquarters IT): Full management of all vehicle devices, setting security policies, and bulk app installations/removals.
- Dispatch Center Administrator: Permissions to view and locate vehicle devices, send task notifications, and view app versions.
- Regional Line Supervisor: Can perform remote reboots and collect logs for devices in their area.
- Driver Role: Limited to using specified business apps, preventing system setting changes or unrelated access.
Device Grouping by Region or Line: Vehicles are grouped based on routes or regions, with corresponding supervisors and dispatchers assigned.
Auditing and Monitoring: All remote actions are logged for auditing and accountability.
Results
- Rapid Issue Resolution: Dispatch centers and regional supervisors can quickly address driver device issues, saving time.
- Security Compliance: Drivers operate with minimal permissions, ensuring safety and data security.
- Cost Efficiency: IT teams focus on system upgrades and process optimization, reducing labor costs.
- Improved Service Quality: Vehicles receive immediate technical support, enhancing operational efficiency and customer satisfaction.
3Case 3: Digital Signage Provider - Unified Yet Isolated Management for Multiple Clients

Company Overview
A company specializing in digital signage solutions for malls, chain stores, and hotel lobbies, using large Android tablets or displays with custom ad playback and central control systems. Clients are mainly chain brands needing to manage their screens.
Challenges
- Multi-Tenant Management: The service model requires independent device management for numerous enterprise clients on a single platform, preventing cross-access to client data.
- App Updates and Content Delivery: Precise delivery of updates and content to specific client devices was challenging without flexible permission control tools.
- Increased Client Self-Service Needs: As clients grew, the need for self-monitoring of screen status and simple operations increased, burdening the technical team.
Solution
Multi-Tier Member Account Creation:
- Super Administrator: Highest management authority, creating and maintaining client sub-accounts, and executing large-scale mode switches or app pushes.
- Client Administrator: Each client manages their digital signage devices, updating content and restarting apps.
- Client Sales or Marketing Staff: Custom permissions for internal teams to reduce IT department involvement.
Device Group Isolation: Each client's devices are grouped, with access limited to the client's administrator account.
Precise App and Content Delivery: Selective updates to specific client screens to avoid business disruptions.
Audit Logs and Troubleshooting: Clients can view operational logs to quickly identify issues and request advanced support.
Results
- Multi-Tenant Efficiency: Enables efficient service for multiple clients on a single platform, avoiding system duplication and security risks.
- Increased Client Engagement: Clients manage their screens, making timely updates without waiting for supplier responses.
- Reduced Internal Support Burden: Only complex technical issues require advanced support, easing operational load.
- Easier Business Expansion: The management model allows for rapid replication of success, showcasing technical and service efficiency.












Leave a Reply.