Network Security Assessment Explanation & How-to Guide
Part 1: What Is Network Security Assessment?
Businesses and enterprises rely on networks to operate and communicate. Therefore, conducting a comprehensive network security assessment is essential to fortify defenses against many network security threats and vulnerabilities.
The process of network security risk assessment involves a thorough assessment and analysis of an organization's network infrastructure to pinpoint vulnerabilities, evaluate threats, and validate safety standards.
It helps businesses to implement robust cybersecurity measures, prevent cyber-attacks and security breaches, and protect critical information and assets. To examine network security threats and vulnerabilities, IT professionals inspect a range of network elements, including routers, switches, firewalls, endpoints, etc., to evaluate their resilience against cyber threats and their capacity to prevent unauthorized access attempts.
Part 2: Purposes of Network Security Assessment
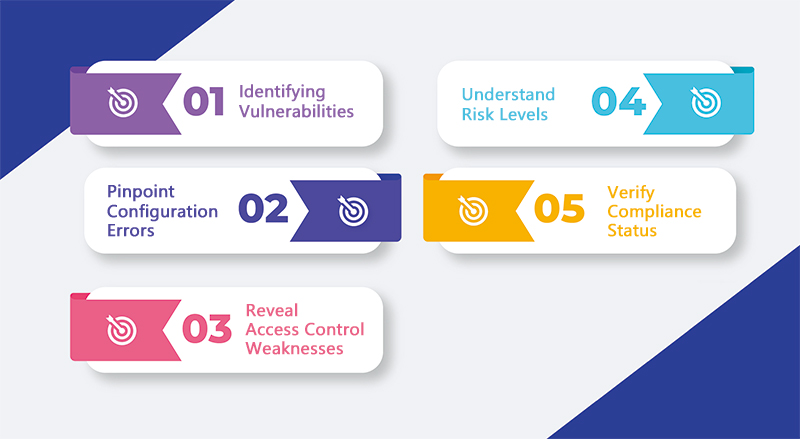
Just like any process, network and security assessment also has aims, goals, and purposes. Let's understand the importance of network security monitoring and analysis and have a deep insight into some of the significant objectives of doing it, such as identifying vulnerabilities in the network, including the hardware and software, pinpointing elements, like routers, switches, firewalls, endpoints, etc., understanding risk levels, and verifying the compliance status.
● Identifying Vulnerabilities in the Network
Network security risk assessment can help enterprises pinpoint potential weaknesses within hardware and software that cyber attackers could exploit. Once you have identified the vulnerabilities, you can take robust cybersecurity measures.
● Pinpoint Configuration Errors
It helps detect network device faults such as routers, firewalls, servers, or endpoints that might compromise enterprise data and cloud security. It prevents unauthorized access to the sensitive data of an enterprise.
● Reveal Access Control Weaknesses
By performing thorough monitoring and assessment, enterprises can find potential external and internal network security threats and lapses in incident response protocols. Understanding the position of vulnerabilities enables the execution of the right actions to eliminate the chances of a breach.
● Understand Risk Levels
You must have a deep insight into the risks and threats related to network security and highlight critical areas. It enables you to prioritize security investments and make necessary amendments to the enterprise network security policy.
● Verify Compliance Status
A thorough risk assessment of an organization's network security helps to ensure adherence to industry standards and cloud and data security policies such as PCI DSS (for credit card processors), GDPR, HIPAA (for healthcare enterprises), and ISO 27001.
Now that we understand the importance of security assessment for an organization's network and data let's discuss different types of network and cloud security risk analysis.
Part 3: Types of Network Security Assessment
One must know the different types to test and analyze an organization's network security. Below, we discuss various network security assessments, such as:
1. Vulnerability Assessment
Vulnerability Assessment offers a thorough check-up of an organization's network infrastructure. It involves scanning the network to find weak spots or vulnerabilities, such as an unpatched software version on critical servers.
The goal is to discover known problems in software, settings, or systems hackers could use to break in. Once the vulnerability is identified, the dedicated IT professional or expert prioritizes, ranks, and reports it accordingly.
2. Risk Assessment
Risk Assessment predicts what could go wrong with an enterprise's cloud, data, or network security. It's about assessing different security risks that might cause trouble and how bad things could get if they happen.
Risk assessment makes it easier to decide which security measures need the most attention and should be dealt with foremost. It sets priorities to keep everything safe and sound.
3. Penetration Testing
Penetration Testing, also known as network security testing, is ethical hacking. It is about simulating an attack on a network to see how safe it is. The goal is to find vulnerabilities by trying different ways a real hacker might use.
Companies bring in ethical hackers or cybersecurity experts to try and break into their network using tricks like social engineering or finding problems in software. The network security testing highlights the importance and benefits of enforcing a robust company network security policy.
4. Compliance Assessment
In simple words, Compliance Assessment is a network rule check. It ensures that a network follows all the essential regulations and standards set by the industry, government, or the company itself. It checks if the network and its safety measures match up with specific rules like PCI DSS (for credit cards), GDPR, HIPAA (for healthcare), ISO 27001, etc. It ensures everyone follows the proper rules to keep things safe and legal.
Combining all network security assessments and testing types can provide a comprehensive view of the network's security posture. It helps enterprises determine precisely what security measures to focus on and make their defenses robust.

Part 4: How to Start the Network Security Assessment
It is quite a complicated task to start a network security assessment. It requires strategic planning and thorough execution. Usually, enterprises rely on a special team to take charge of this job.
It might involve many IT experts from the company's tech team, a security-focused squad, or a blend of both. It relies on how the organization is set up and what it needs to ensure its network stays secure. Let's understand some of the crucial steps to performing network security assessment in detail:
1. Define the Scope of Assets and Create an Inventory List
The foremost step in starting a network security assessment is defining the scope and creating an inventory list of assets and systems that need to be assessed. Some of the critical assets are:
● Network Devices: Routers, switches, firewalls, load balancers, and wireless access points
● Servers: Web servers, file servers, database servers, mail servers, DNS servers, and other physical and virtual servers hosting vital services
● User Endpoints: All user devices, including workstations, laptops, and mobile devices
● Network Security Systems: Firewalls, intrusion detection systems (IDS), intrusion prevention systems (IPS), and security information and event management systems (SIEMS)
● Cloud Assets: All cloud-based services, data storage, and applications
● Software: Vital software and applications used by the enterprise
● Data: Sensitive customer and employee data, intellectual property (IP), and storage locations
Along with these, some other vital assets like remote access systems (including VPNs), physical security systems, and IoT devices should also be on the checklist.
Once you have specified the scope and created an inventory list of assets, it is also essential to define the timeframe to get an accurate estimation of the length of the network assessment.
2. Establish an Audit Plan
After defining the scope and timeframe, the next step is establishing an audit plan. It helps to outline the following things:
3. Start Network Security Risk Assessment
Once you have created the roadmap and audit plan, it's time to start the network security analysis. To do so, you must perform various steps, including creating asset documentation, ranking assets, using assessment tools, evaluating security risks, and checking compliance. Let's discuss these steps in detail:
Step 1. Create Asset Documentation.
It is essential to thoroughly document all the network assets you have defined in the scope, including their names, types, locations, owners, and functions.
Step 2. Categorize and Rank Assets.
You have to categorize and rank the documented assets. It can be done based on various criteria like asset value, business importance, and vulnerability levels.
Step 3. Use Assessment Tools.
It is crucial to select the most suitable assessment tool to determine the possible network vulnerabilities. Below, we discuss some of the primary assessment tools to perform network assessments:
Assessment tools
- For Automated Network Scanning: You can use tools like Nessus, Qualys, Retina, and OpenVAS for comprehensive and automated network scanning.
- For Penetration Testing: You can use tools like Nmap, Arp-Scan, and Gophish for network security testing. These tools help to simulate an attack on your enterprise network using frameworks like social engineering (pen testing trick to test employees' adherence to network security policies).
- For Code Review: For code review, enterprises can use tools like Veracode and analyze security risks or flaws in application & system code.
- For Configuration Check: Assess system, application, and network configurations for potential vulnerabilities using tools like SolarWinds.
- For Threat Modeling: Forecast and examine potential threats to the network using tools like IriusRisk, OWASP Threat Dragon, and Microsoft Threat Modeling Tool.
Step 4. Assess Prioritize Security Risks
Each vulnerability is of a different level. Hence, it is important to assess and prioritize the identified vulnerabilities. To do so, you have to specify the potential threats, apprehend the possible impact, forecast the likelihood of occurrence, and then calculate their risk levels.
You can use tools and models like CVSS (Common Vulnerability Scoring System) and DREAD (Damage, Reproducibility, Exploitability, Affected Users, Discoverability).
Step 5. Ensure Compliance with Network Security Policies
Ensure that the network assets abide by the internal network security policies, like access control and password policies, along with the standard industry regulations.
4. Generate a Report and Remediation Plan
The next step is to report the results of the network security assessment so that an enterprise can create a remediation plan. The report must be thorough, including details of all the identified risks, assessment methods performed, and tools used. It helps to generate and apply a robust and comprehensive remediation plan.
However, it's not over yet. Once you have initiated the remediation plan, make sure to follow up to avoid any further network security breaches and risks.
We have now covered enterprise network security testing, assessment, and analysis. Every organization must deeply understand its network security posture to tackle any vulnerabilities, risks, and cyber-attacks. A robust network security prevents institutions from both financial and intellectual property losses.
Still need help? Submit a request >>


