Use AirDroid Business to streamline IT resources, reduce cost, and increase efficiency
Use AirDroid Remote Support to provide 1-to-1 remote assistance & troubleshooting for clients, staffs, and business partners
Make AI robots your intelligent business assistant
Explore AirDroid Business Partner Programs to help you grow your business
Sells industry-leading MDM and remote control solutions
Drive more high-value leads for AirDroid Business
Offer AirDroid Business as a subscription service to your customers
Join the distribution program, generate revenue growth
Integrate AirDroid Business to your devices, strengthen products and services

Employees copy or share data on corporate devices to personal devices via USB transfer or other means.
When corporate devices are lost or stolen, it is necessary to completely wipe all sensitive data in them.
Employees using corporate devices for non-work purposes, such as installing entertainment apps, will lead to lower productivity.
Configure mandatory authentication policy for devices, such as lock screen password, to protect device and data security.
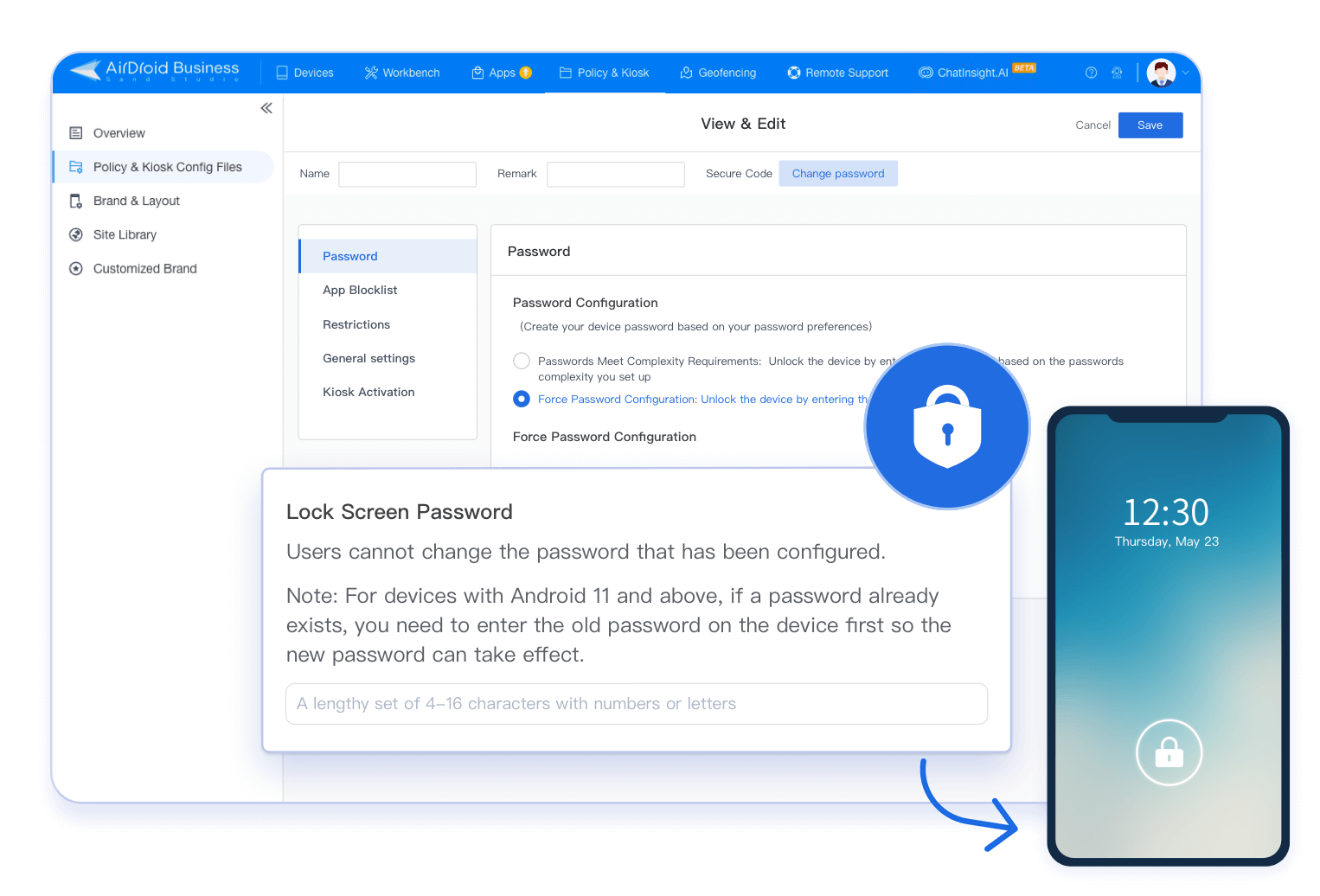
Enforce lock screen password rules (complexity, validity date, repetition limits, and more) to protect your organization's devices from unauthorized usage.
Blocklist/allowlist features and in-app browser blocking enable precise control over runnable apps, satisfying diverse organizational needs.
IT can remotely enforce the configuration of VPN on devices e.g., a corporate VPN, ensuring secure access and transmission of corporate data.
Allow only select google accounts to set up Android device after factory reset to prevent potential misuse of device if it gets lost or stolen.
Digital certificate management allows administrators to upload,push & verify digital certificates remotely for device authentication on Android devices.
Limit device functions like profile access, factory settings, file transfer, network sharing, SIM settings, call whitelist, and contact management to meet various device needs.
Provide WiFi, language, time zone, APN, and other settings to let the device run in the specific environment that you build.

Medical institutions use mobile devices to monitor patients' health as well as manage their electronic medical records and prescription history. However, when the device is lost, the patient's private data may be compromised. By deploying AirDroid Business' mobile device security policy, such as enabling preset password rules and usage restrictions on USB connection, the data can be effectively protected.

IT service providers that offer managed services for attended Android devices need to ensure that their clients’ devices are always secure and under control. Using a series of Device Security Restrictions, such as prohibiting the installation of apps from unknown sources and enforcing data encryption, will ensure safety, compliance and data integrity. When the device runs abnormally, the data can be erased through the security policy to prevent data leakage.

Due to their business needs, logistics companies usually equip their fleet of vehicles with mobile devices. If the driver violates the company’s regulations by breaking away from location tracking and using the device for non-work purposes, it may result in unnecessary data usage and eventually cause financial losses to the company. By disabling the hardware and software buttons on the device and using the application blocklist function, such violations can be effectively avoided, while preserving data integrity.
There's more productivity to explore